Credential Stuffing 2.0: The Use of Proxies, CAPTCHA Bypassing
Por um escritor misterioso
Descrição
Welcome to the new age of cyber attacks, where hackers have taken credential stuffing to the next level. Meet Credential Stuffing 2.0, where the use of proxies, CAPTCHA bypassing, CloudFlare security, and GUI tools have become the norm..
Protecting Against Credential Stuffing: Lessons from the Paypal Breach
The Ultimate Guide to Avoiding CAPTCHAs in Web Scraping
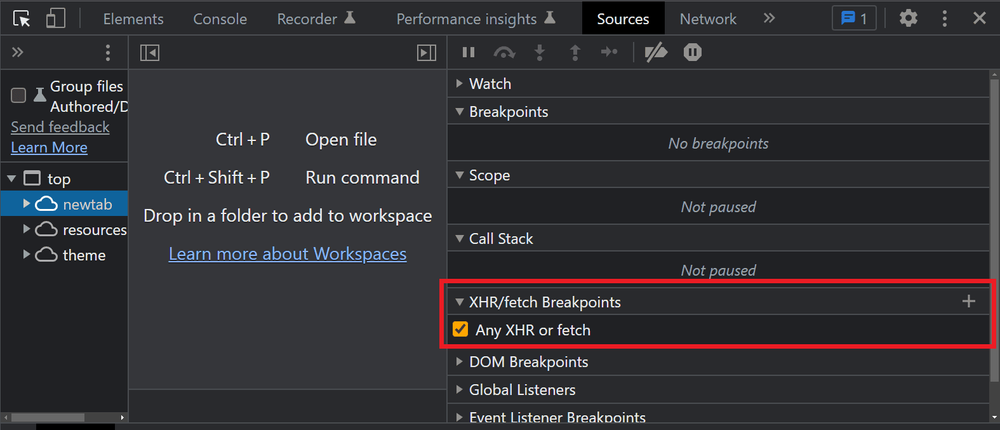
How to Bypass Cloudflare in 2023: The 8 Best Methods - ZenRows

How Credential Stuffing is Evolving - PasswordsCon 2019
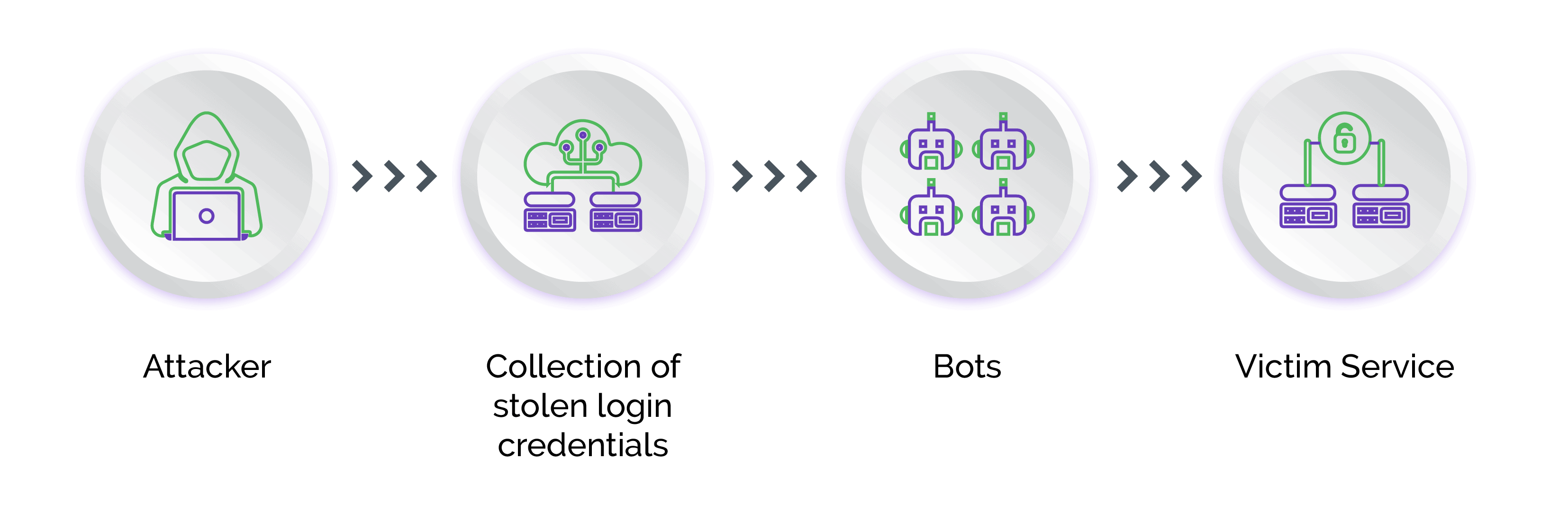
What Is Credential Stuffing?
Credential stuffing: definition, affected industries

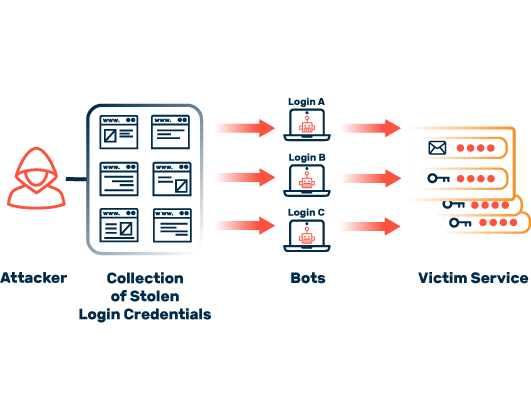
Email Compromise with Credential Stuffing Attack Tools
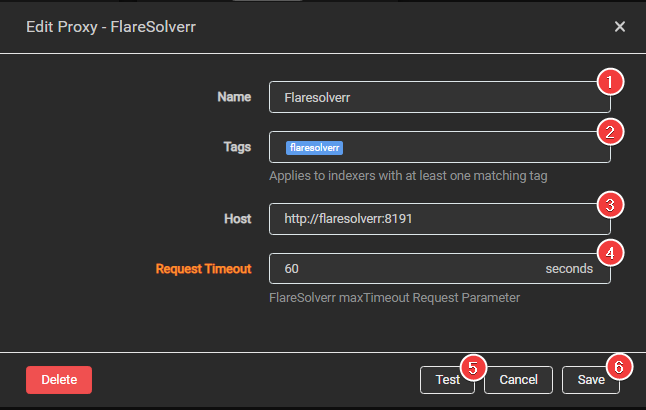
How to Bypass Cloudflare Bot Protection? Web Scraping Service in 2023
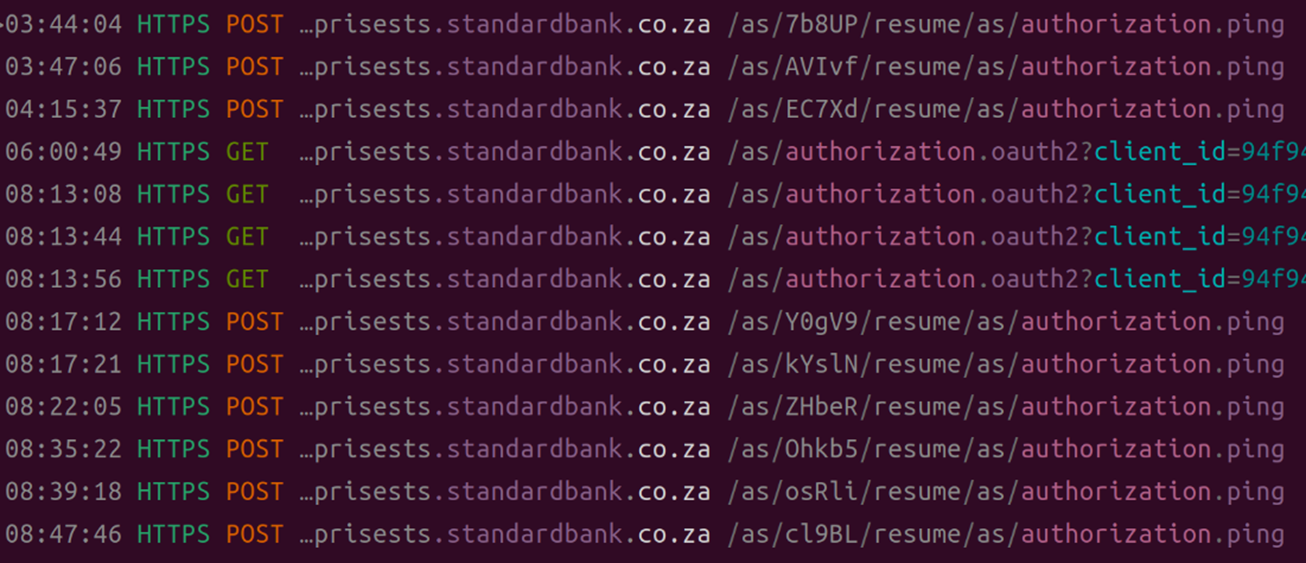
How Residential Proxies and CAPTCHA-Solving Services Become Agents of Abuse - Security News - Trend Micro IE
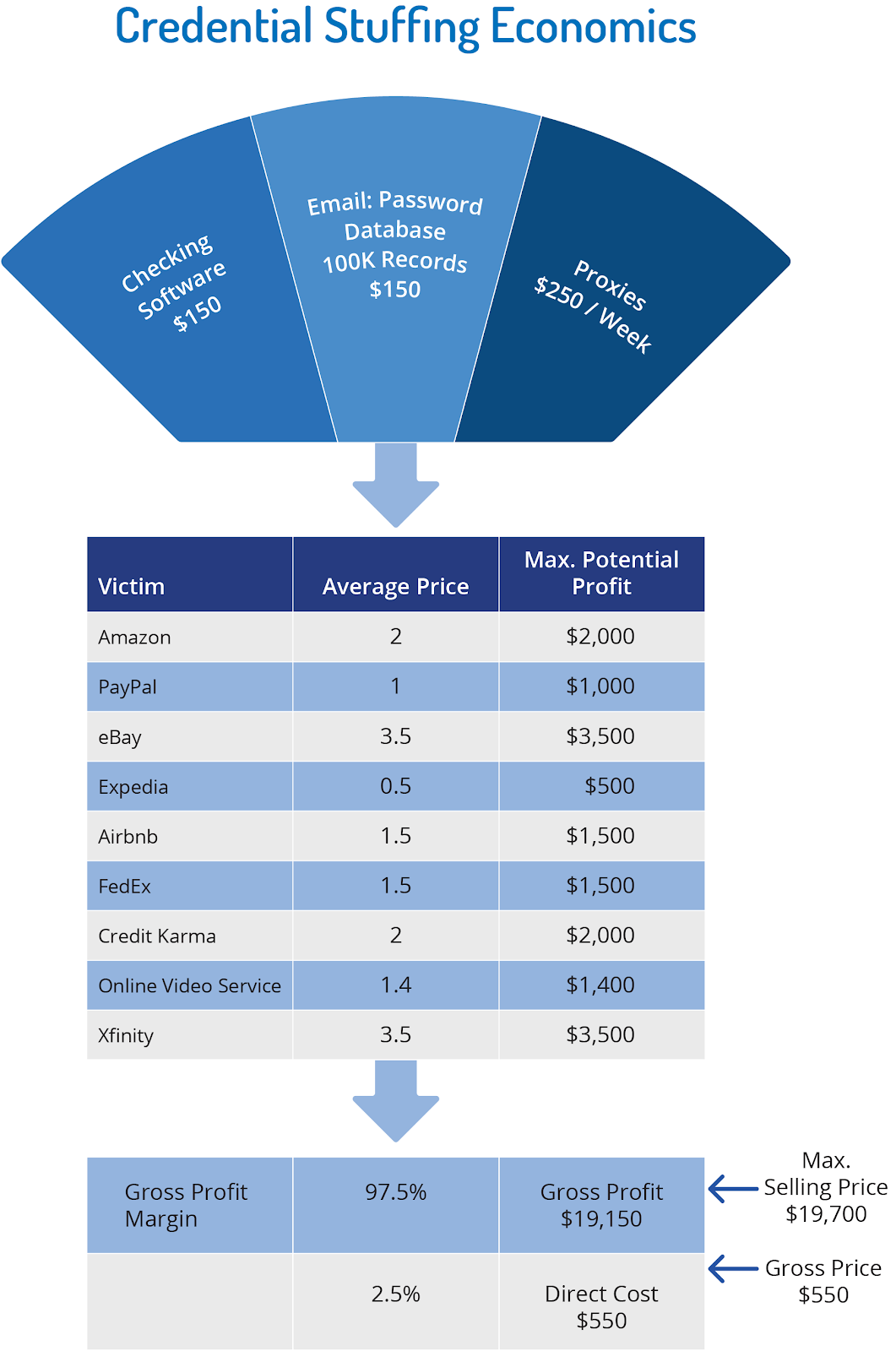
The Anatomy of Highly Profitable Credential Stuffing Attacks

How Google Cloud can help stop credential stuffing attacks

What Is Credential Stuffing?

Email Compromise with Credential Stuffing Attack Tools
de
por adulto (o preço varia de acordo com o tamanho do grupo)







