Advanced Apple Debugging & Reverse Engineering, Chapter 31
Por um escritor misterioso
Descrição
In this chapter, you'll use DTrace to hook objc_msgSend's entry probe and pull out the class name along with the Objective-C selector for that class. By the end of this chapter, you'll have LLDB generating a DTrace script which only generates tracing info for code implemented within the main executable that calls objc_msgSend.

Advanced Apple Debugging & Reverse Engineering (3rd Edition) - 2018

How to Reverse Engineer an iOS App, by Zafar Ivaev
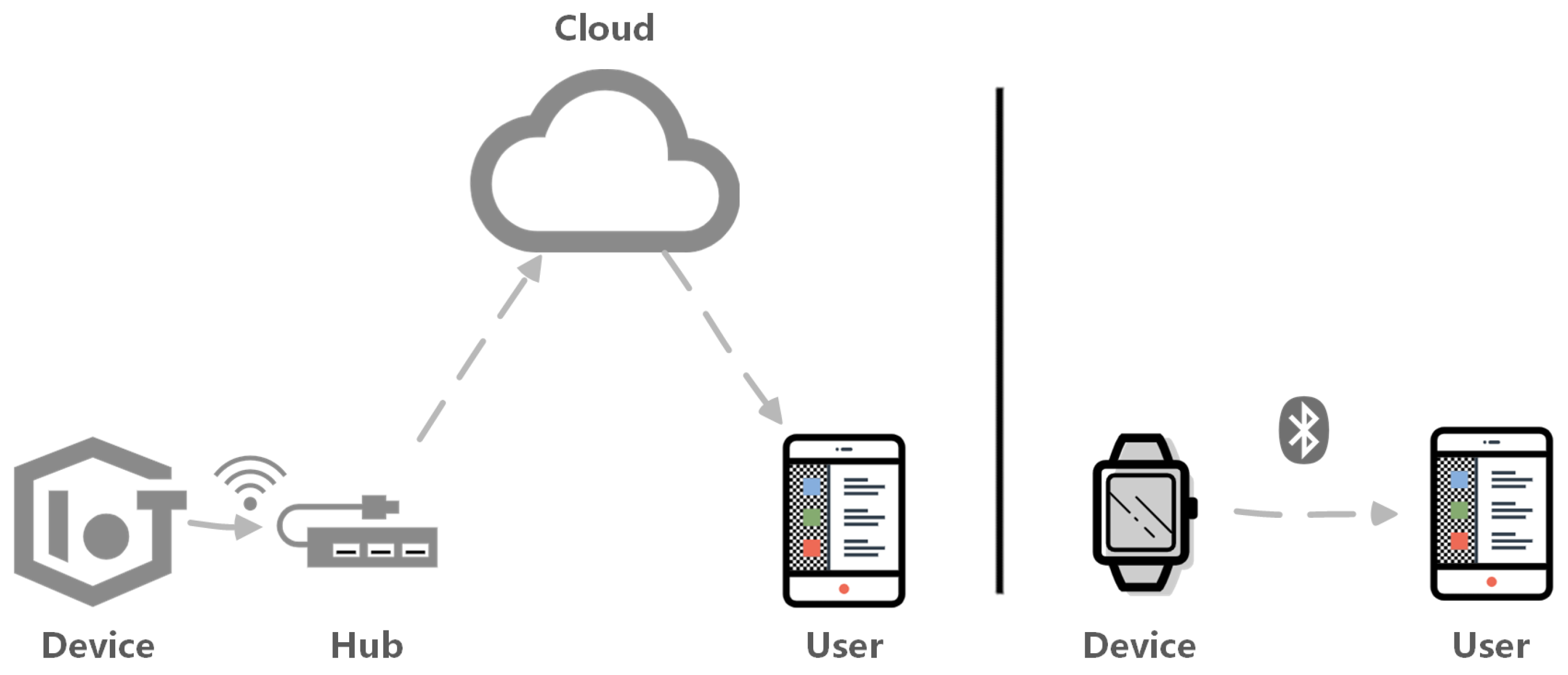
Future Internet, Free Full-Text
IOS Reverse Engineering - Configuring LLDB
Used Book in Good Condition Highlight, take notes, and search in the book

Practical Reverse Engineering: x86, x64, ARM, Windows Kernel, Reversing Tools, and Obfuscation

Advanced Apple Debugging & Reverse Engineering, Chapter 11: Assembly Register Calling Convention

Advanced Apple Debugging & Reverse Engineering, Chapter 31: DTrace vs. objc_msgSend

Kodeco Learn iOS, Android & Flutter

Advanced Apple Debugging & Reverse Engineering

HACKER SUMMER CAMP 2023 GUIDES — Part Nine: DEFCON 31, by DCG 201
de
por adulto (o preço varia de acordo com o tamanho do grupo)