Cryptojacking - Cryptomining in the browser — ENISA
Por um escritor misterioso
Descrição
The technique of hijacking browsers for mining cryptocurrency (without user consent) is called

Cryptojacking (@cryptojacking) / X

Other 3,700 MikroTik Routers compromised in cryptoJacking campaigns
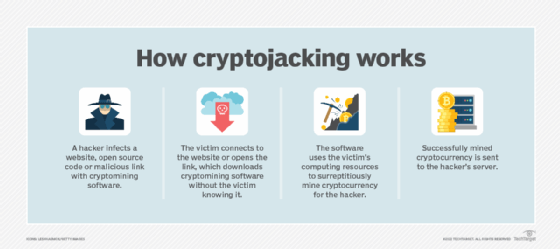
What is Cryptojacking? Detection and Preventions Techniques
Are you seriously using CoinImp?! · Issue #660 · joemccann

The Anomali Blog

Cybersecurity Briefing A Recap of Cybersecurity News in

What is cryptojacking and how does it work?

PacNOG 23: Introduction to Crypto Jacking
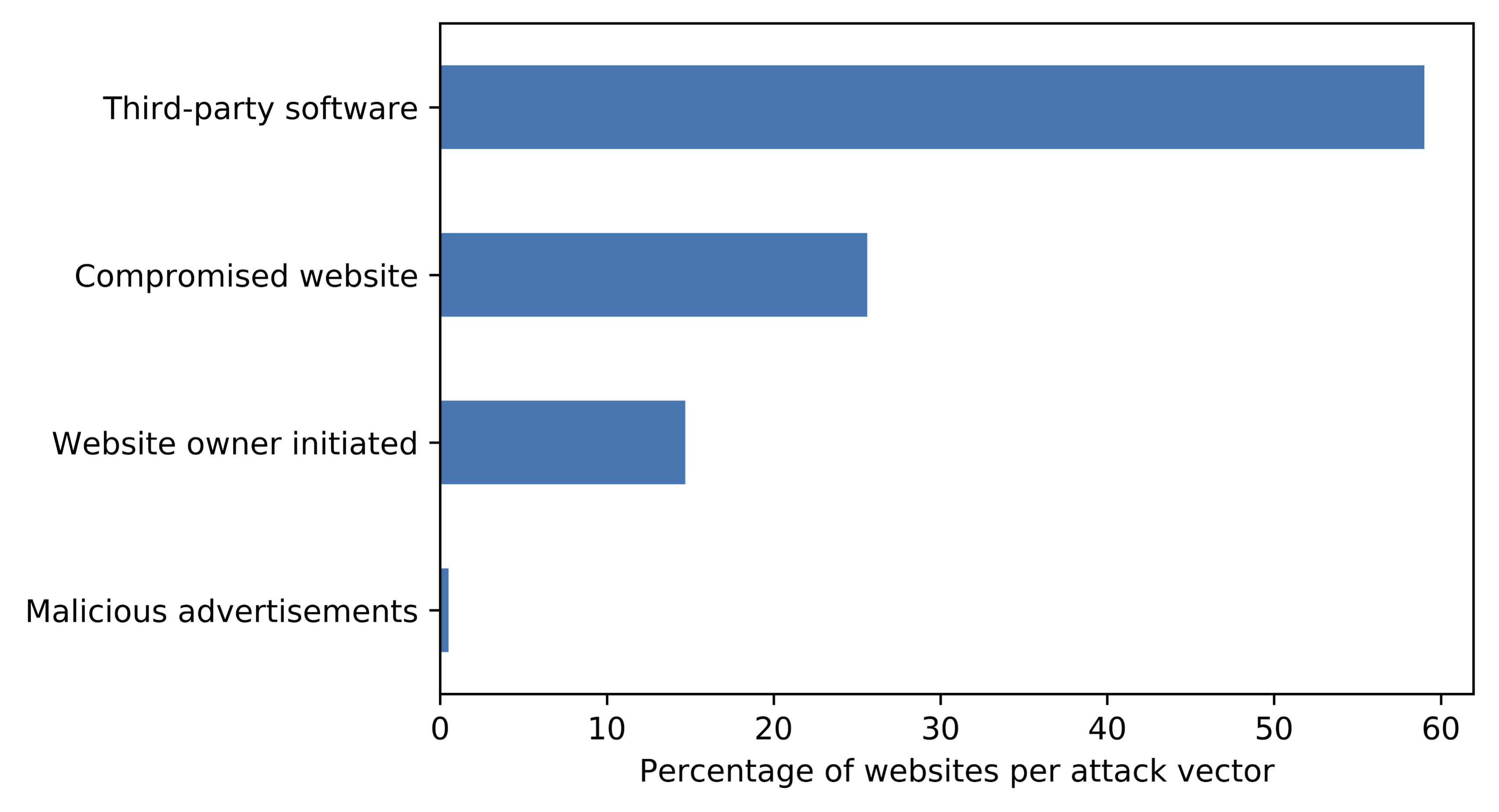
Blog: Infected third-party software key driver for cryptojacking

The concept of cryptojacking and how it works?

MrbMiner cryptojacking campaign linked to Iranian software firm

ENISA Threat Landscape 2022, PDF, Malware
de
por adulto (o preço varia de acordo com o tamanho do grupo)

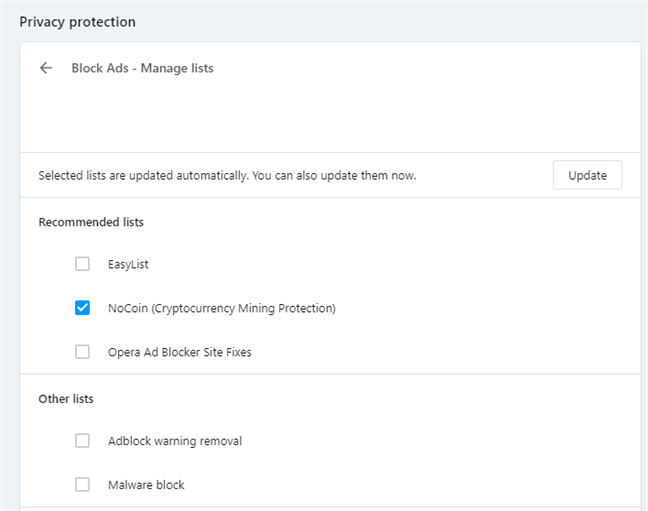
/cdn.vox-cdn.com/assets/1283378/TWC.jpg)




