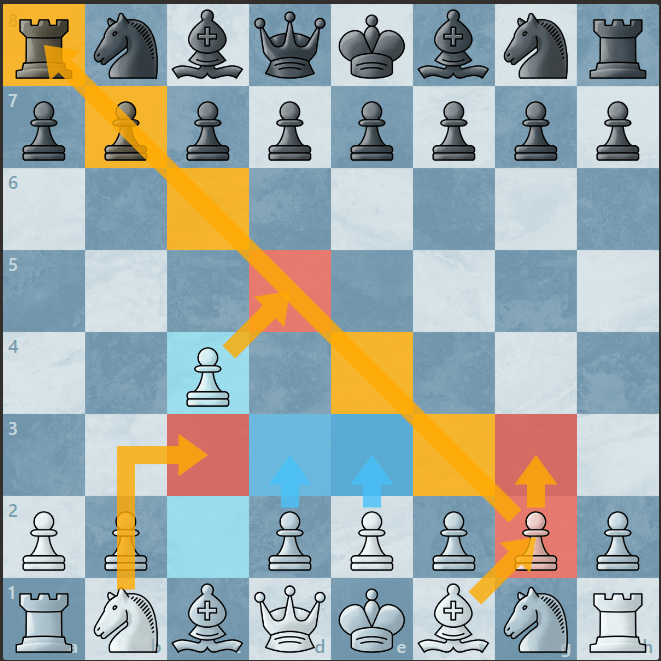
Abusing Jenkins Groovy Script Console to get Shell, by Nishant Sharma
Por um escritor misterioso
Descrição
Memcached Recon with Nmap, Metasploit and Memc-tools
Linux Privilege Escalation]Breaking out of a Restricted Shell
Exploiting Buffer Overflow vulnerability to do Privilege
Analyzing Memory Dump with Volatility II
Weak Portainer Credentials to Docker Host takeover
Recovering SSH keys from Docker image
Analyzing firmware image using Binwalk
CVE-2020–7991] CSRF in Adive Framework
CVE-2020-8772 Exploitation under 3 minutes
12 Useful DNS Queries with Dig. Lab Scenario
Linux Security] Understanding Linux Capabilities Series (Part I
de
por adulto (o preço varia de acordo com o tamanho do grupo)