Rundll32: The Infamous Proxy for Executing Malicious Code
Por um escritor misterioso
Descrição
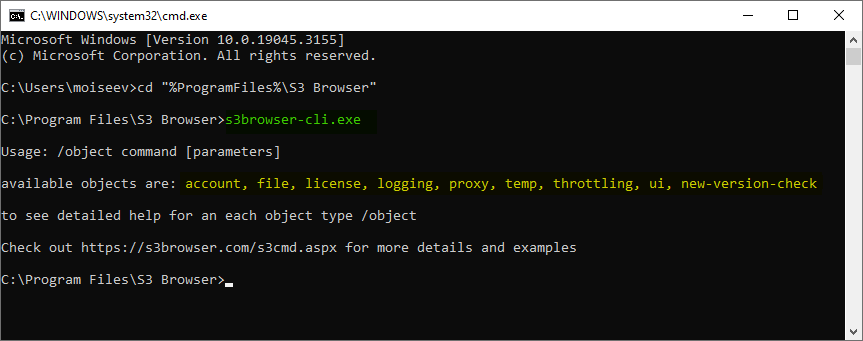
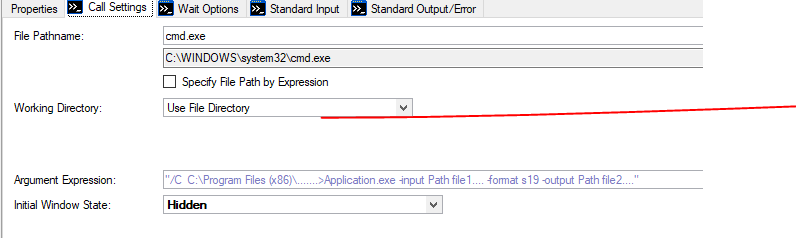
Take a deeper dive into an often abused Microsoft-signed tool, the infamous rundll32.exe, which allows adversaries to execute malicious code during their offensive operations through a technique which we explain in detail
Lemon Duck brings cryptocurrency miners back into the spotlight

Silvio R. (@Pinas_) / X

Living Off the Land: How to Defend Against Malicious Use of Legitimate Utilities
Emulating the Infamous Modular Banking Trojan BokBot - AttackIQ

Detecting IcedID: The Latest Campaign Against Ukrainian Government Bodies - SOC Prime

Persistent pests: A taxonomy of computer worms - Red Canary

themed campaigns of Lazarus in the Netherlands and Belgium

4 malicious campaigns, 13 confirmed victims, and a new wave of APT41 attacks
themed campaigns of Lazarus in the Netherlands and Belgium
de
por adulto (o preço varia de acordo com o tamanho do grupo)