Malware analysis Suspicious activity
Por um escritor misterioso
Descrição

Malware Analysis: Static vs. Dynamic and 4 Critical Best Practices
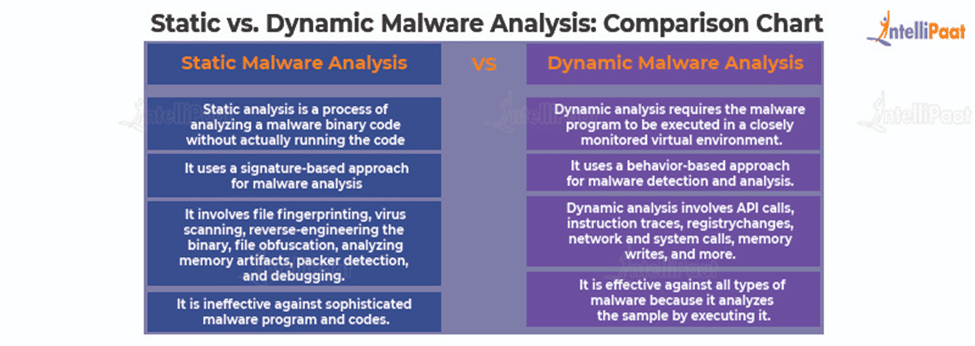
Malware Analysis - What is, Benefits & Types (Easily Explained)
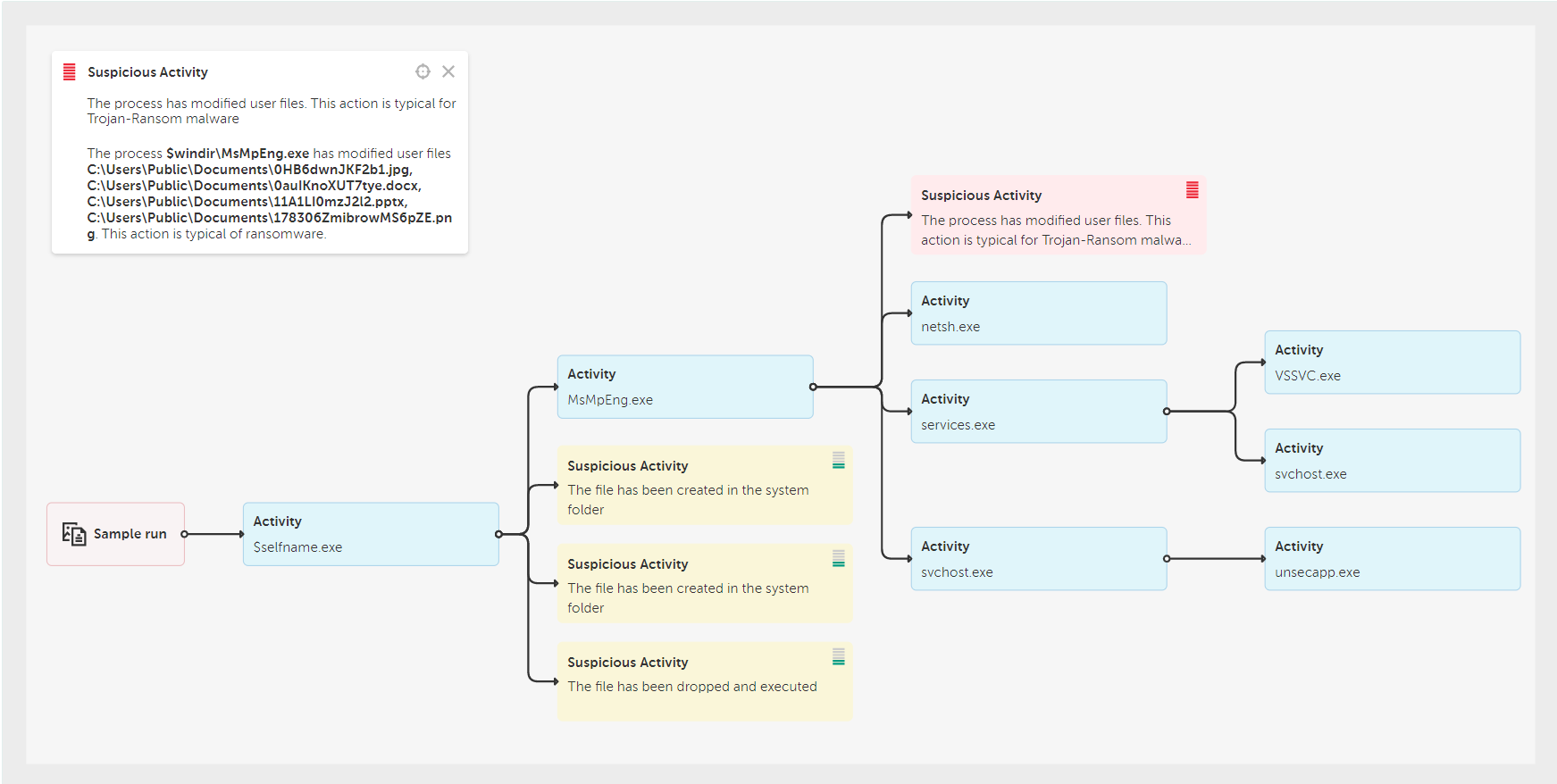
REvil ransomware attack against MSPs and its clients around the

How Malware Analysis Works - NetWitness Community - 669511

Malware Detection: 7 Methods and Security Solutions that Use Them

How to Detect New Threats via Suspicious Activities

Dismantling ZLoader: How malicious ads led to disabled security

The Top 20 Malware Analysis Tools for 2024
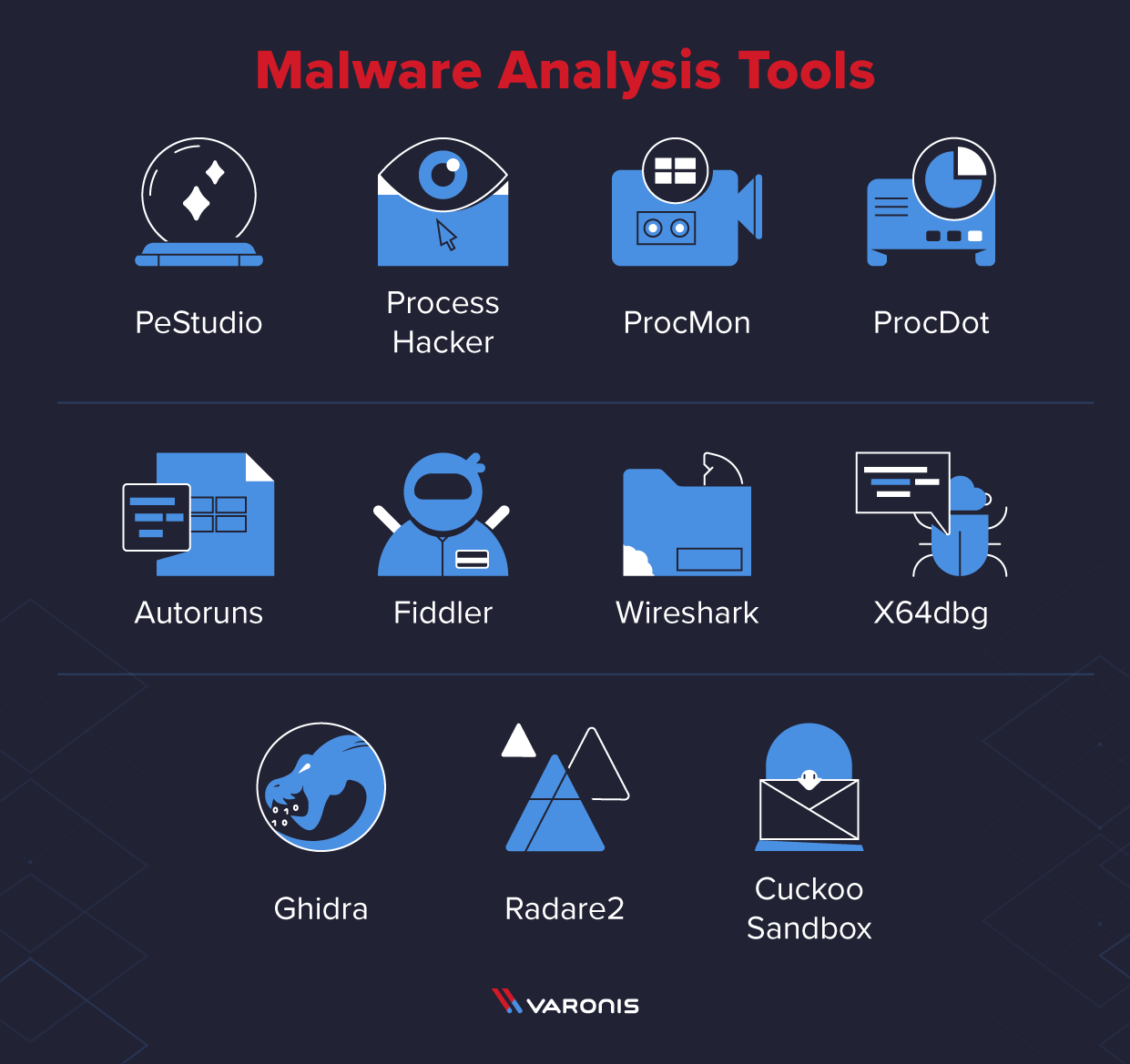
11 Best Malware Analysis Tools and Their Features
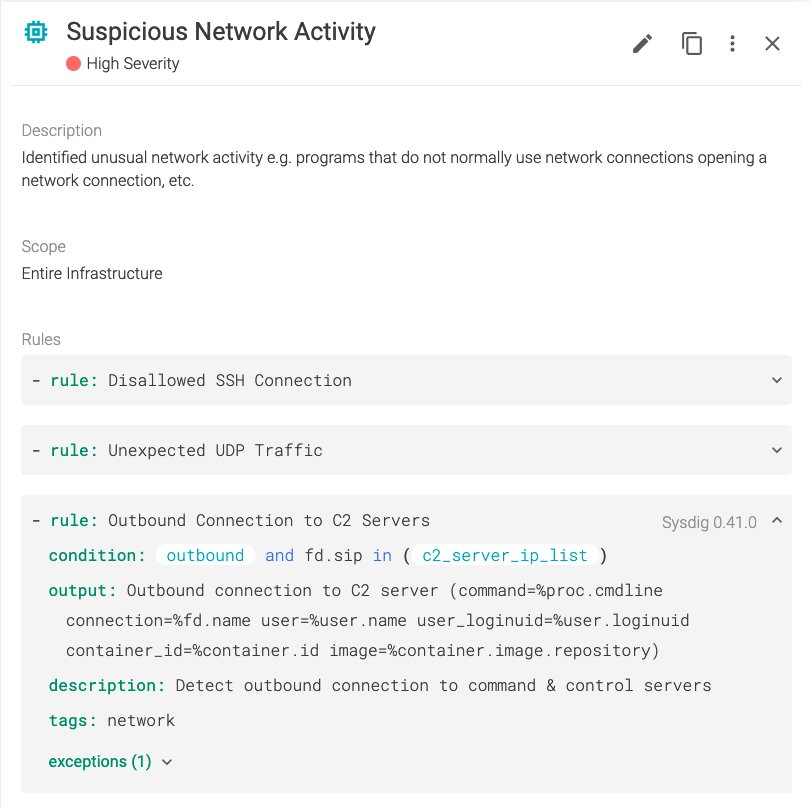
Malware analysis: Hands-On Shellbot malware – Sysdig
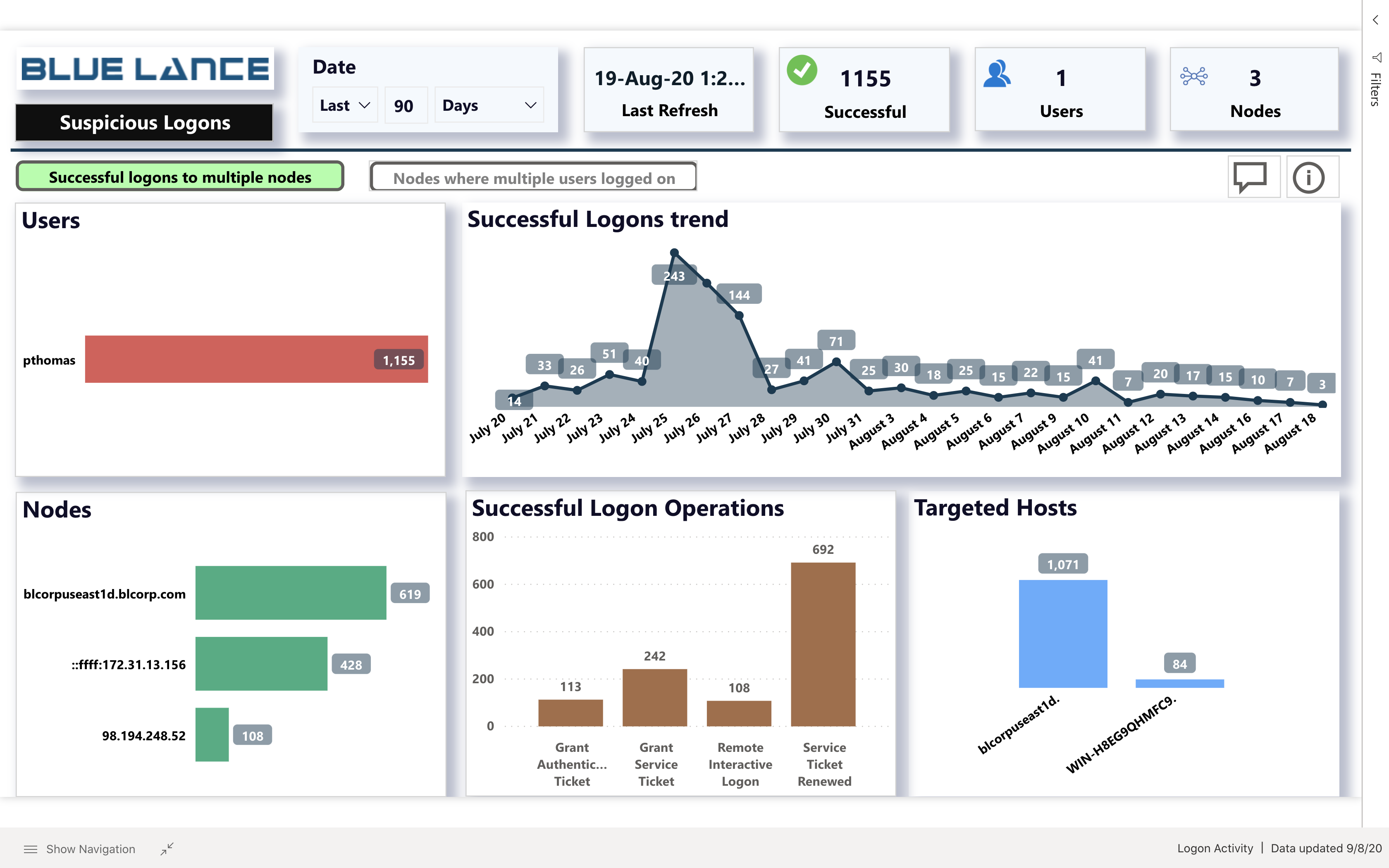
Suspicious Successful Logon Analysis
Monitoring for indicators of ransomware attacks - Splunk Lantern

Malware Analysis: Steps & Examples - CrowdStrike

Fileless malware threats: Recent advances, analysis approach

Advanced Malware Detection – Signatures vs. Behavior Analysis
de
por adulto (o preço varia de acordo com o tamanho do grupo)







