Do Not Cross The 'RedLine' Stealer: Detections and Analysis
Por um escritor misterioso
Descrição
The Splunk Threat Research Team provides a deep dive analysis of the RedLine Stealer threat and shares valuable insights to help enable blue teamers to defend against and detect this malware variant.

Do Not Cross The 'RedLine' Stealer: Detections and Analysis

Redline Stealer/Amadey Bot - Static Analysis and C2 Extraction
Crossing the Line: Unit 42 Wireshark Quiz for RedLine Stealer
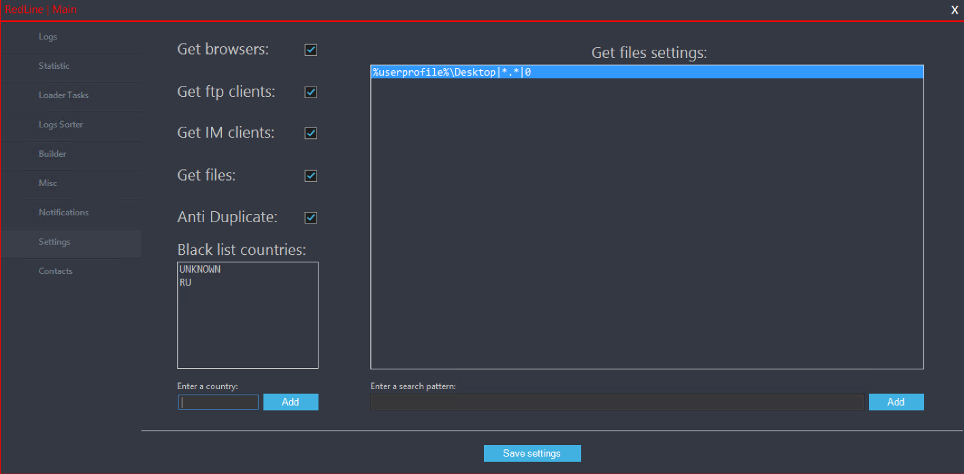
RedLine Stealer Malware - Password Stealer Virus
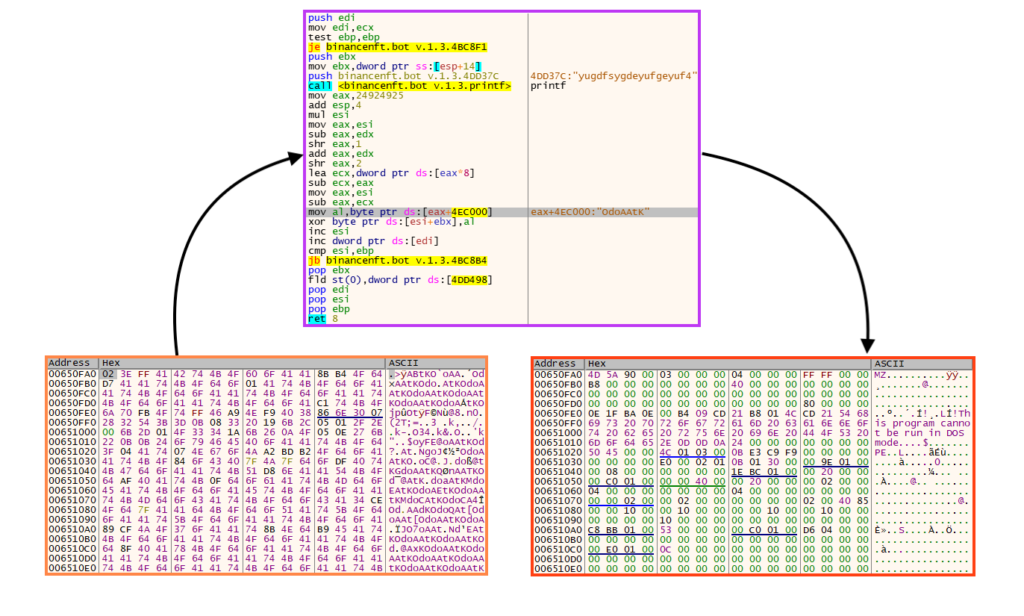
RedLine Stealer Campaign Using Binance Mystery Box Videos to Spread GitHub-Hosted Payload - Netskope
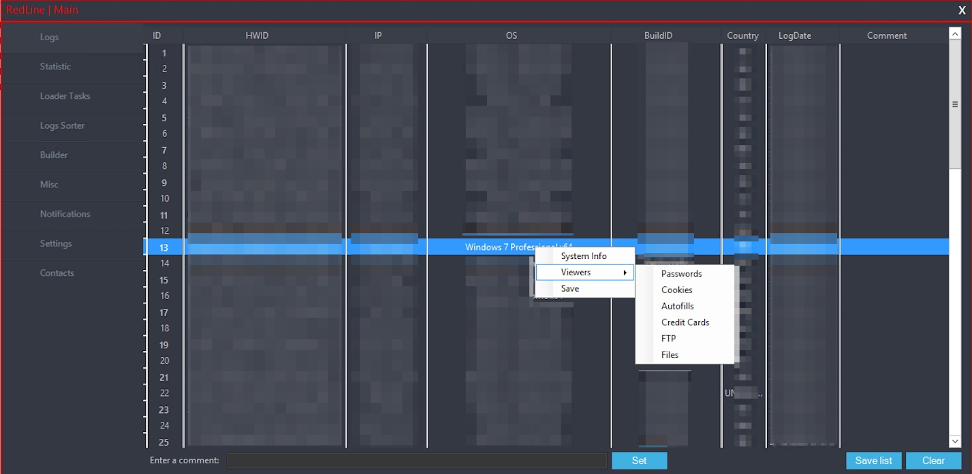
RedLine Stealer Malware - Password Stealer Virus

Do Not Cross The 'RedLine' Stealer: Detections and Analysis

Do Not Cross The 'RedLine' Stealer: Detections and Analysis
From ChatGPT to RedLine Stealer: The Dark Side of OpenAI and Google Bard - Veriti
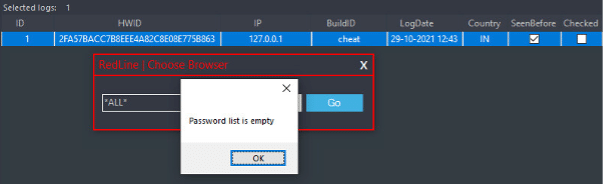
Preventing Credential Theft by RedLine Stealer Malware - Attivo Networks
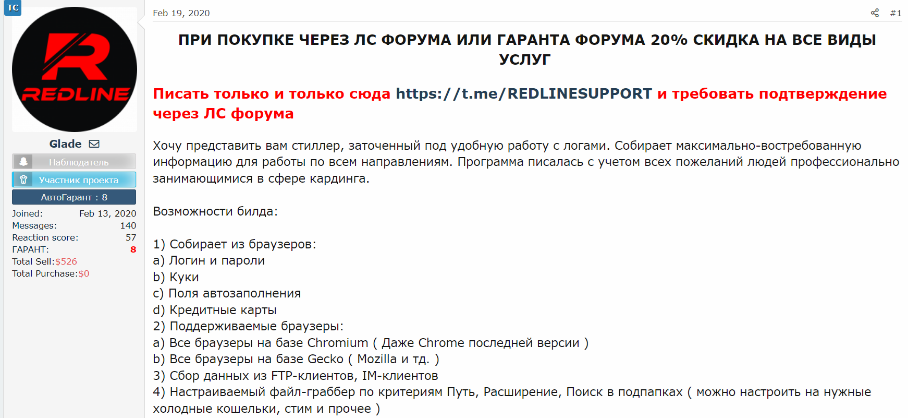
The Next Generation of Info Stealers • KELA Cyber Threat Intelligence
de
por adulto (o preço varia de acordo com o tamanho do grupo)