Microsoft Encrypted Restricted Permission Messages Deliver Phishing
Por um escritor misterioso
Descrição
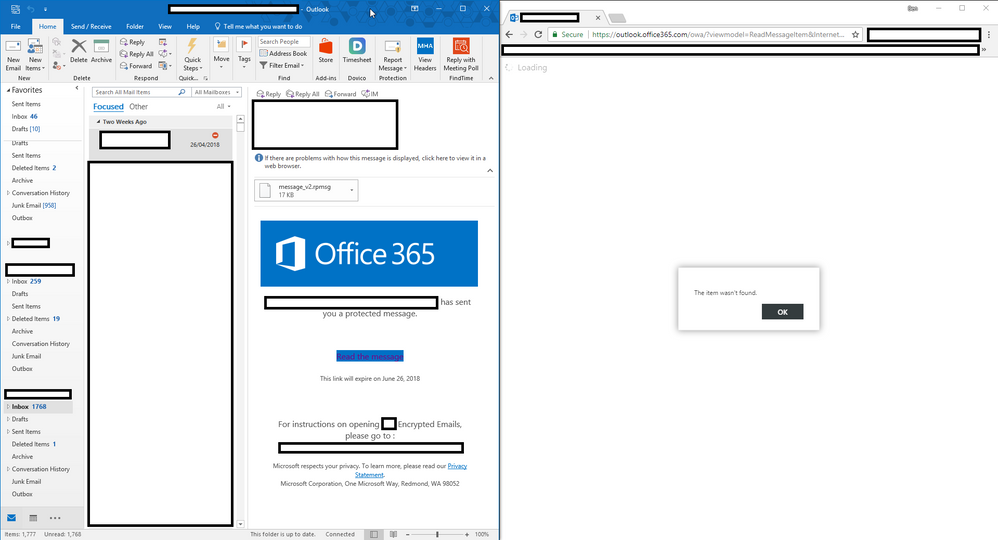
Over the past few days, we have seen phishing attacks that use a combination of compromised Microsoft 365 accounts and .rpmsg encrypted emails to deliver the phishing message.

Email - Wikipedia

View email security reports
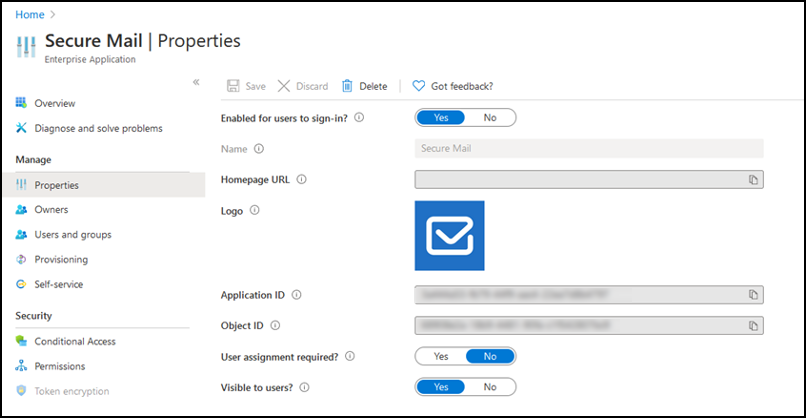
iOS and Android features for Secure Mail
Email encryption in Office 365 - IT Portal

Targeted phishing attacks exploit encrypted RPMSG messages in Microsoft 365

Michele Rotondo on LinkedIn: Microsoft Encrypted Restricted Permission Messages Deliver Phishing

Microsoft Encrypted Restricted Permission Messages Deliver Phishing

Encrypted RPMSG Exploited In Microsoft 365 Phishing - Cybersecurity News
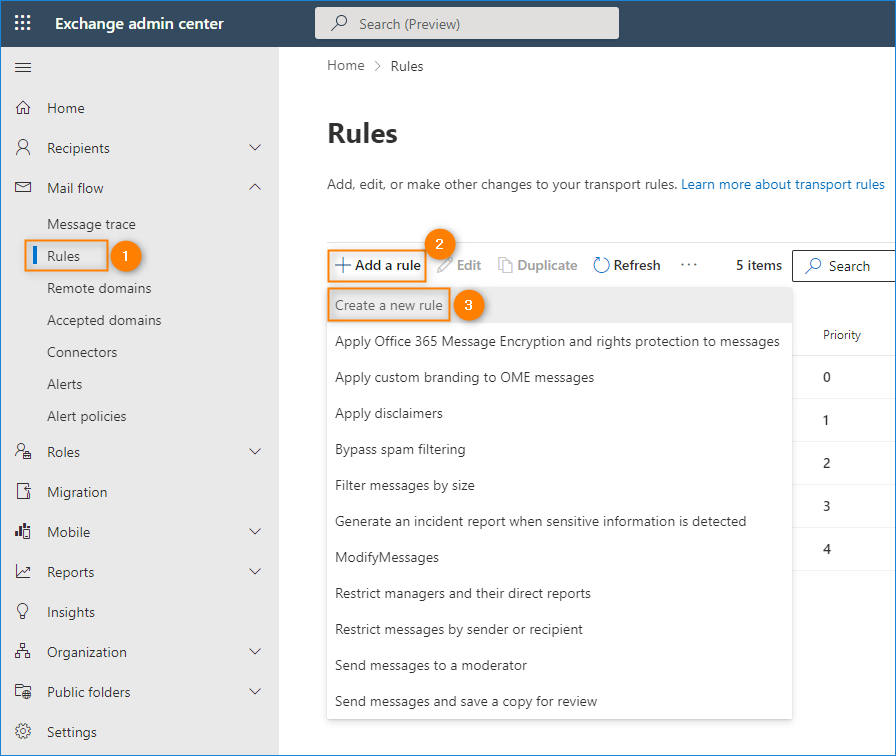
How to block outgoing emails with mail flow rules in Office 365

Microsoft delivers comprehensive solution to battle rise in consent phishing emails
cybersecurity Archives - SOC 2, ISO 27001, HIPAA, NIST, Data Privacy, CMMC, PCI, GDPR
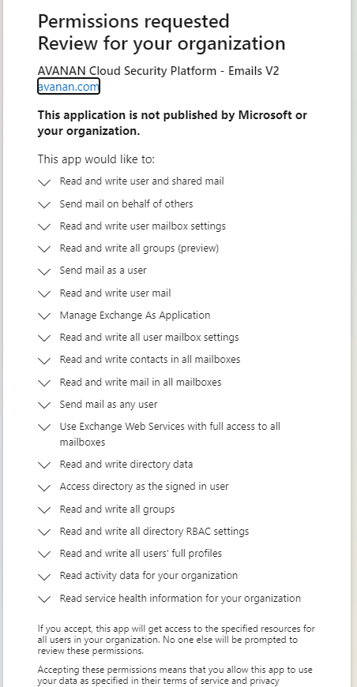
SaaS Security - Activating Office 365 Email
Encrypt only rolling out starting today in Office 365 Message Encryption - Page 2 - Microsoft Community Hub

Sign over Your Hashes – Stealing NetNTLM Hashes via Outlook Signatures, NCC Group Research Blog
de
por adulto (o preço varia de acordo com o tamanho do grupo)







