Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
Por um escritor misterioso
Descrição
Did you know that the Secure Shell protocol, better known as SSH, is not as secure as its name suggests? In this post I show you different ways to attack this protocol. %

Hack The Box - Monitors Walkthrough - Steflan's Security Blog

Explained: The Tinyman Hack (January 2022)
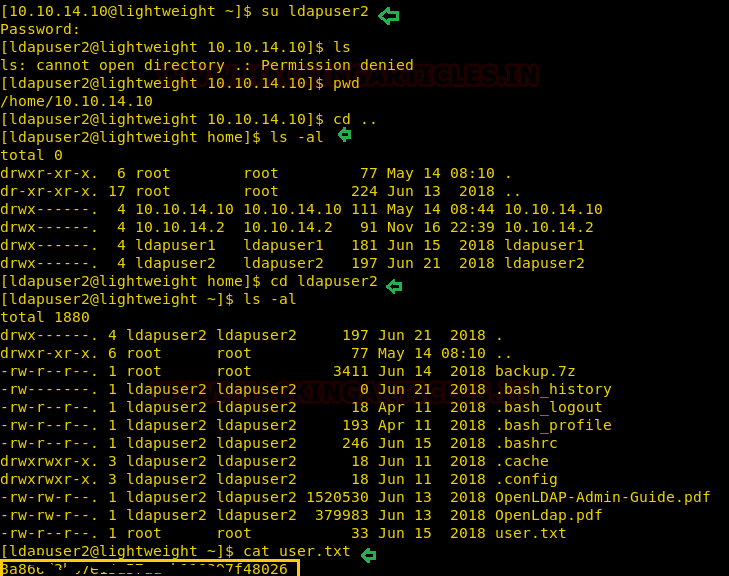
Lightweight: Hack the Box Walkthrough - Hacking Articles

Your IT Provider Is Letting Hackers Into Your Business”

Whois Lookup Ethical Hacking
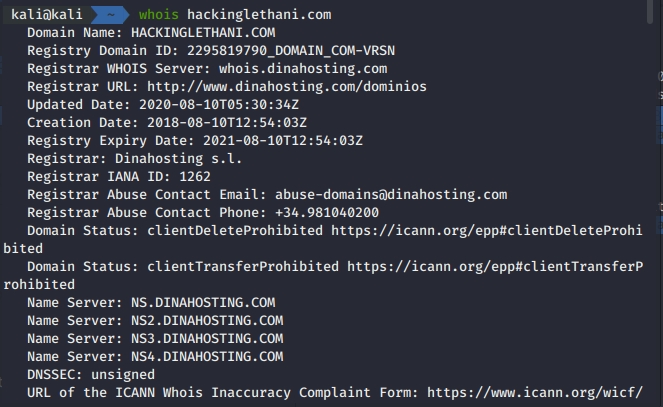
Infrastructure Hacking: WHOIS Protocol » Hacking Lethani

Hacking Tutorial - Ethical Hacking Tutorial - Wikitechy

2600: The Hacker Quarterly (Volume 5, Number 1, Spring 1988), PDF, Broadcasting

Hezbollah's cyber unit hacked into telecoms and ISPs

Linux Challenges - Cyber Security / Ethical Hacking

Playing with FHIR? Don't get burned, white-hat hacker cautions

tl;dr sec] #169 - Top 10 Web Hacking Techniques of 2022, Finding Malicious Dependencies, Fearless CORS
de
por adulto (o preço varia de acordo com o tamanho do grupo)