window.open(url, name) is vulnerable to XSS with name collision · Issue #262 · w3c/html · GitHub
Por um escritor misterioso
Descrição
Xiaoran Wang (xiaoran@attacker-domain.com) This is a joint research with Travis Safford. window.open(url, name, [args]) makes it easy for websites accepting user supplied URLs to be vulnerable when attackers can cause a collision on the
Installing support for WebDAV to access documents in Documents storage in Control Center or from File Explorer – NiceLabel Help Center
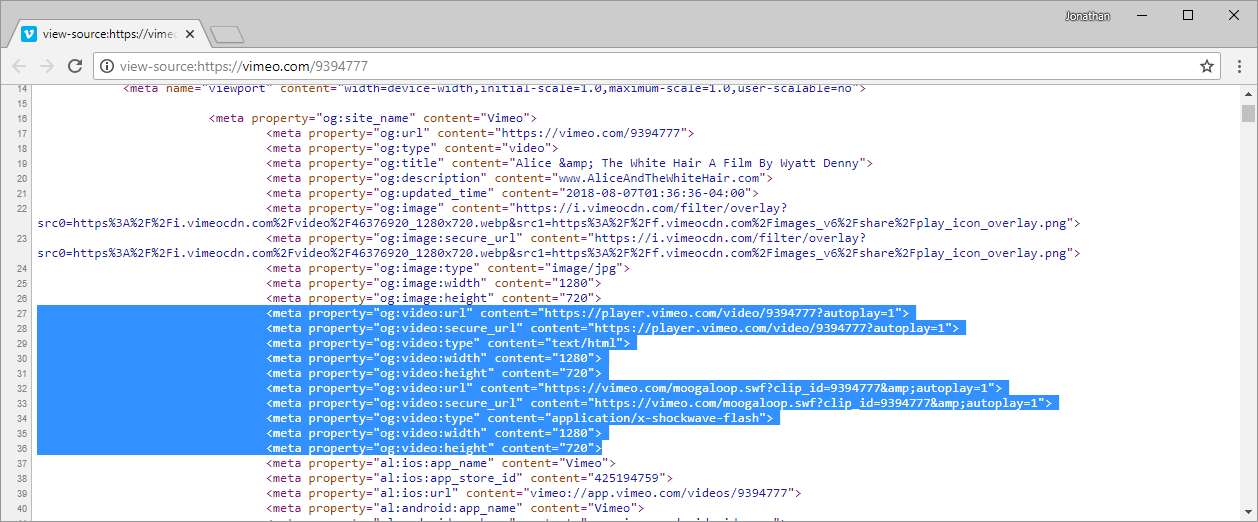
Persistent XSS (unvalidated Open Graph embed) at LinkedIn.com, by Jonathan Bouman

Mutation XSS in Google Search

Automating Discovery and Exploiting DOM (Client) XSS Vulnerabilities using Sboxr — Part 3, by Riyaz Walikar
GitHub - inforkgodara/xss-vulnerability: Explanation of Cross-site Scripting (XSS) with PHP mini project.
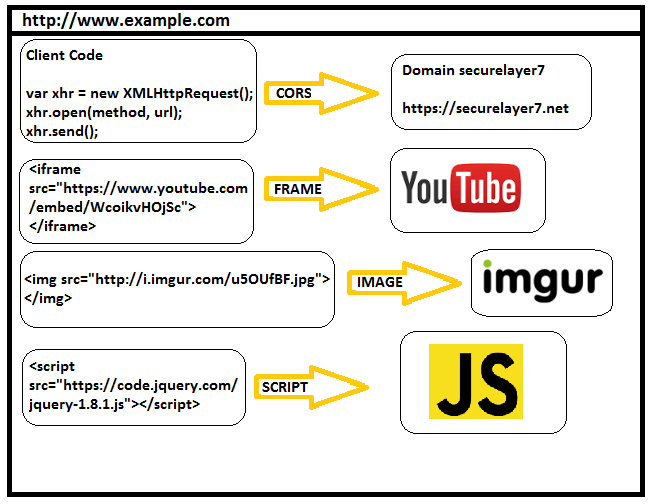
OWASP Top 10 : Cross-Site Scripting #3 Bad JavaScript Imports
Warning] Stored XSS in TwoNav v2.0.28-20230624 · Issue #3 · tznb1/TwoNav · GitHub

Pre-Authentication
Open-Redirect-Payloads/Open-Redirect-payloads.txt at master · cujanovic/Open-Redirect-Payloads · GitHub
de
por adulto (o preço varia de acordo com o tamanho do grupo)






