Complete vulnerability scanning and security consulting competitively priced with no bloated extra offerings or aggressive up-sales. Easy pricing with your choice of reporting and followup support.
Por um escritor misterioso
Descrição

How To Plan & Develop An Effective Cyber Security Strategy

Articles
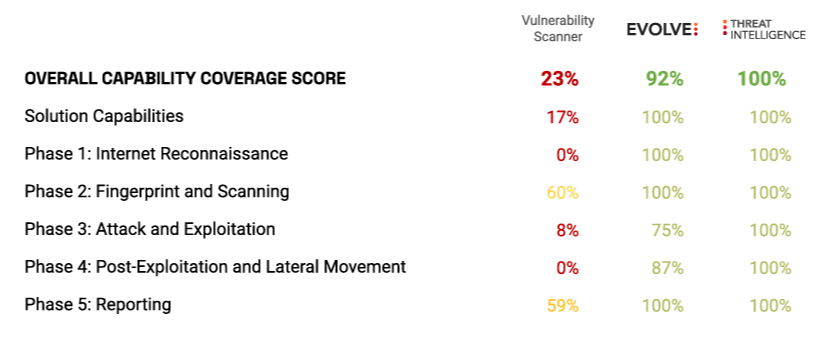
Prioritizing Vulnerabilities : A Risk Based Approach

The Newsletter 57 by International Institute for Asian Studies - Issuu
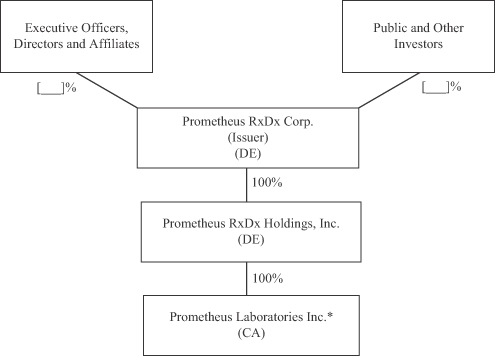
Amendment No. 16 to Form S-1
Preservation and the New Data Landscape - Columbia GSAPP

HIV Glasgow 2018, 28–31 October 2018, Glasgow, UK - 2018 - Journal
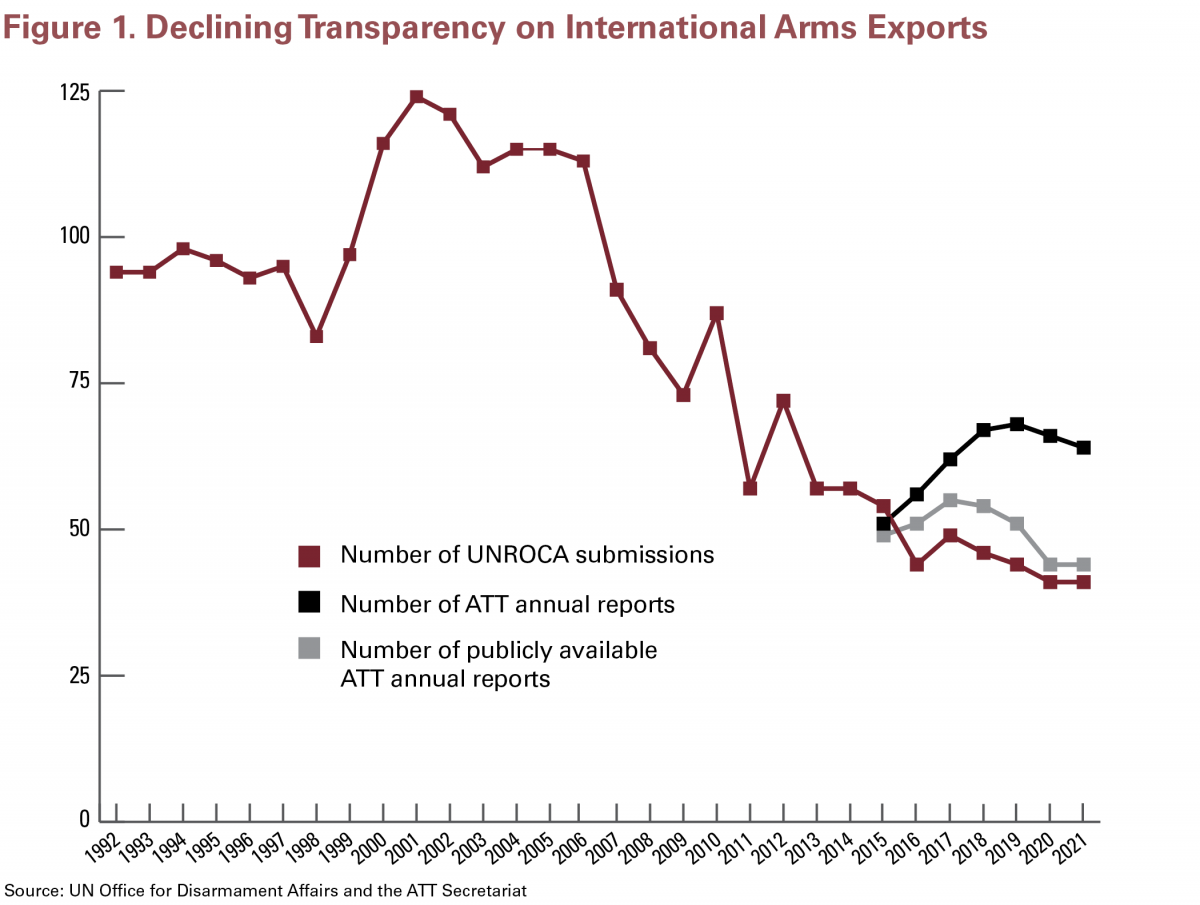
Features Arms Control Association
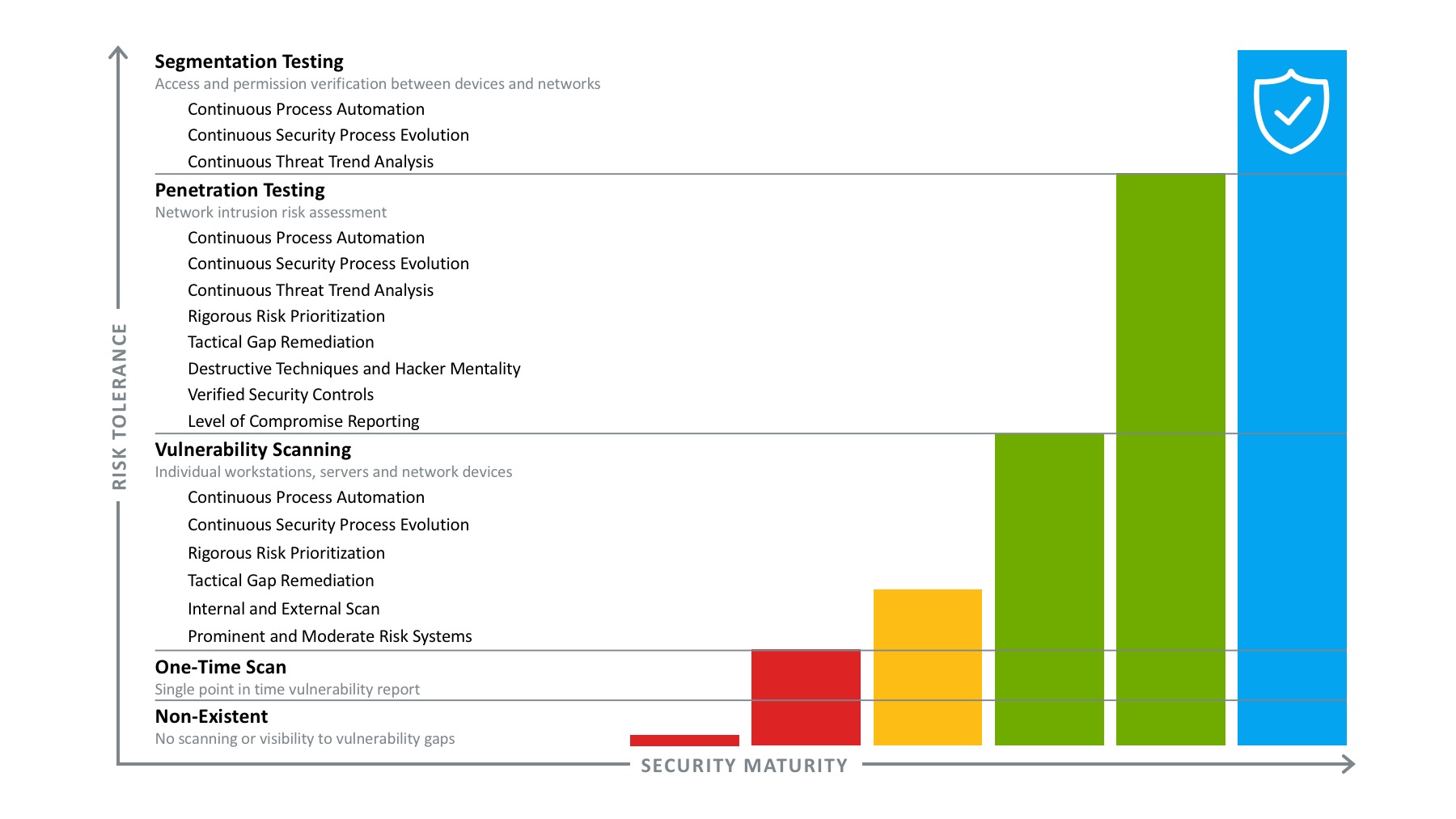
Cloud Security & Managed Vulnerability Scanning in Texas & Oklahoma
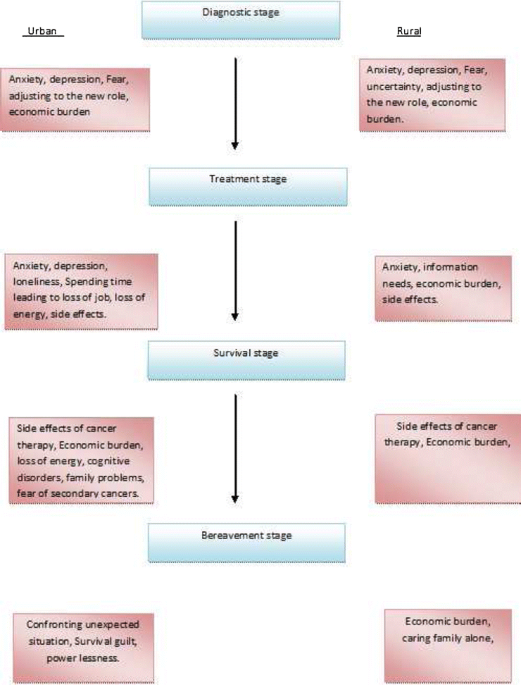
MASCC 2013 Abstracts

HIV Glasgow 2018, 28–31 October 2018, Glasgow, UK - 2018 - Journal

Five Critical Institutional Areas for Tanzania's Development (Part
de
por adulto (o preço varia de acordo com o tamanho do grupo)