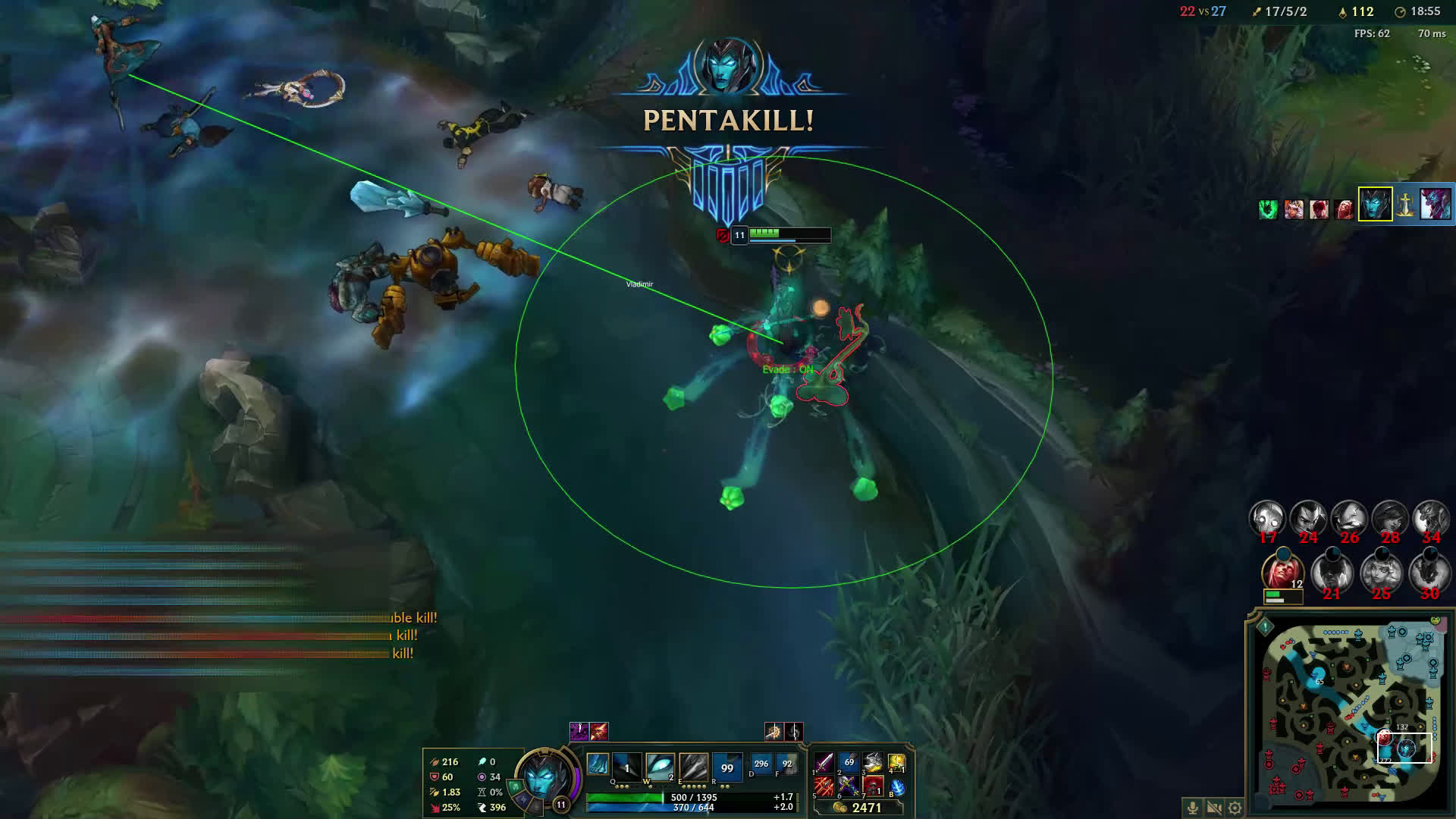
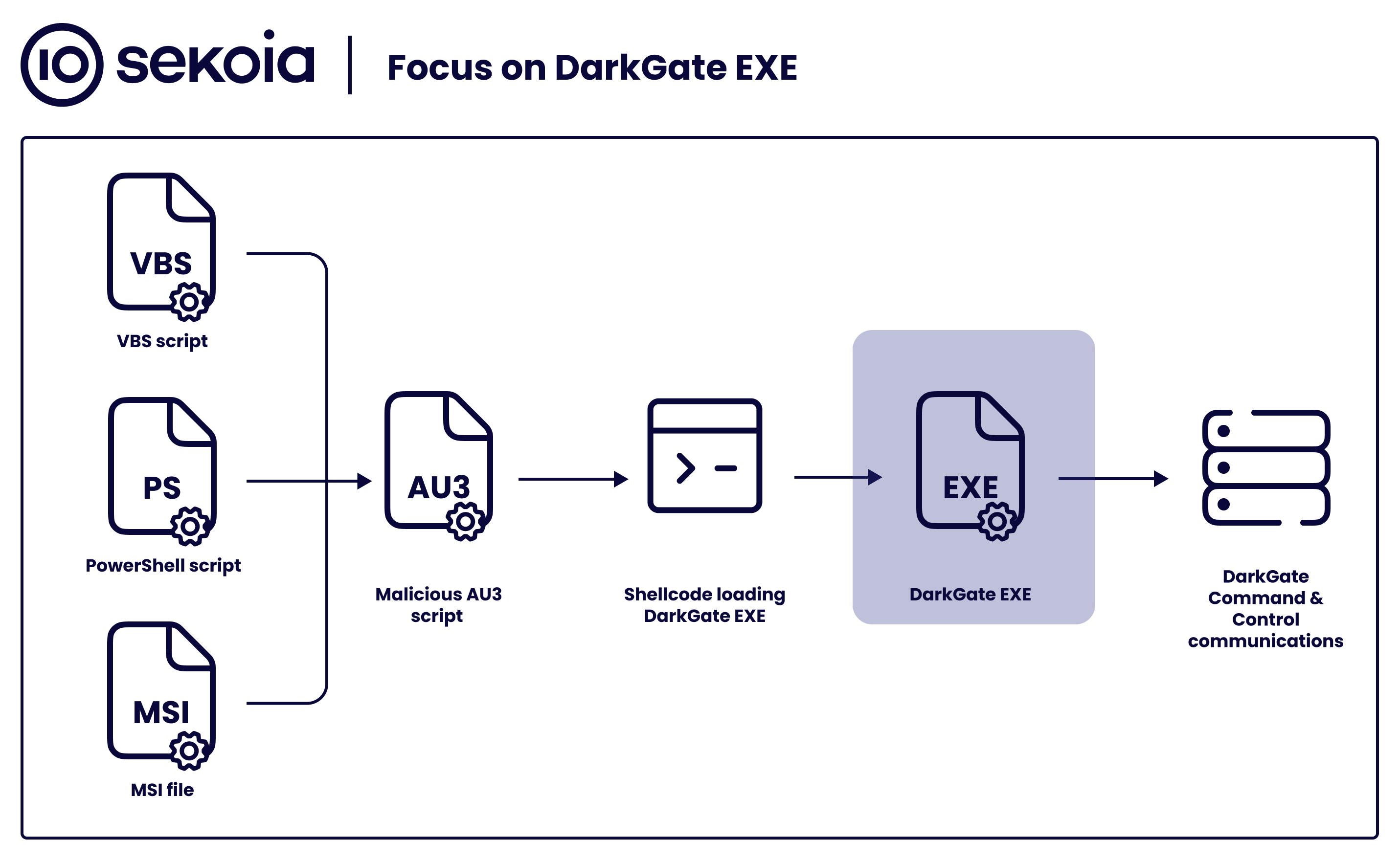
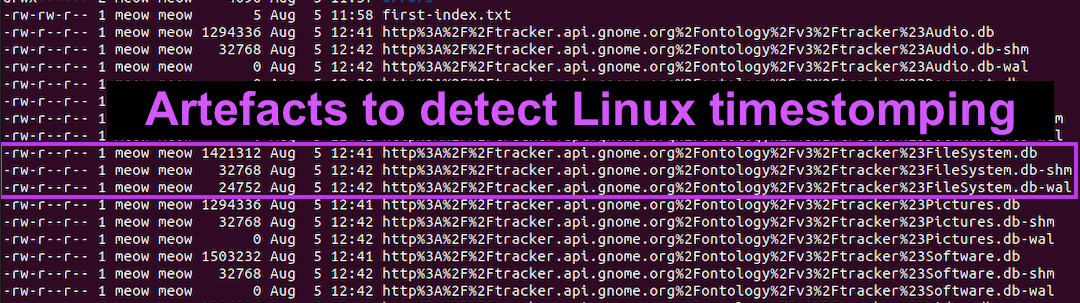
Cybercriminals are shapeshifting to evade security controls
Por um escritor misterioso
Descrição

Remote Access Trojans: What You Need to Know and How to Protect Yourself – BizTech Lens
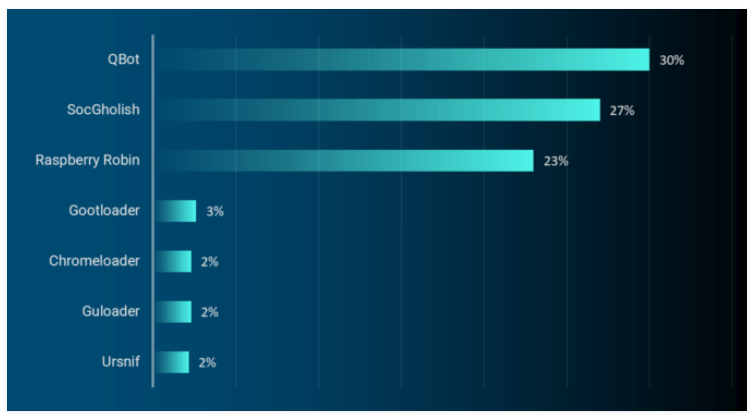
Inside the FBI and DOJ Takedown of Qakbot, the “Swiss Army Knife” of Malware

Future/Tense: Trend Micro Security Predictions 2023 - Security Predictions
%20(1).jpg)
Top Cybersecurity Threats 2023: What Businesses Must Know
Sifting strains to understand the threat of military targeted malware - Army Technology
Inside the FBI and DOJ Takedown of Qakbot, the “Swiss Army Knife” of Malware

Why Application Security is Critical to Network Security

Proposed “Cyber Security Agency Organization” chart for Turkey

Spooky cyber risks haunting organisations: safeguard your data this Halloween

3 Basic Security Practices Will Protect Your DNS From Compromise IT Infrastructure Advice, Discussion, Community - Network Computing

Demystifying the Shapeshifters of Cybercrime: Unveiling the Secrets of Metamorphic and Polymorphic Malwares

Shape-shifting malware: a chameleon of cyber threats. How does it work?, Tehreem Satti posted on the topic

APG Threat Digest: 17th Edition - Blackpoint Cyber
de
por adulto (o preço varia de acordo com o tamanho do grupo)
_new-roblox-evade-script-hack-gui-124-auto-farm-124-god-mode-124-infinite-money-amp-more-pastebin-2022-preview-hqdefault.jpg)