How to enforce consistent code scanning rules across Checkov and
Por um escritor misterioso
Descrição
Learn how to create customized and consistent code security scanning rules across the Bridgecrew platform and Checkov.

Mostly Technical

Securing Cloud-Native Applications in DevSecOps

Terraform Security Best Practices – Sysdig

Embracing the Future: Unlocking Efficiency with Security as Code

Checkov: Security & Compliance for Infrastructure-as-Code

Prioritize, skip, and fail with policy severities in Checkov - Bridgecrew Blog

Securing the Cloud: TPM Strategies for Cloud Security

Infrastructure as Code (IaC) Scanning for Vulnerabilities
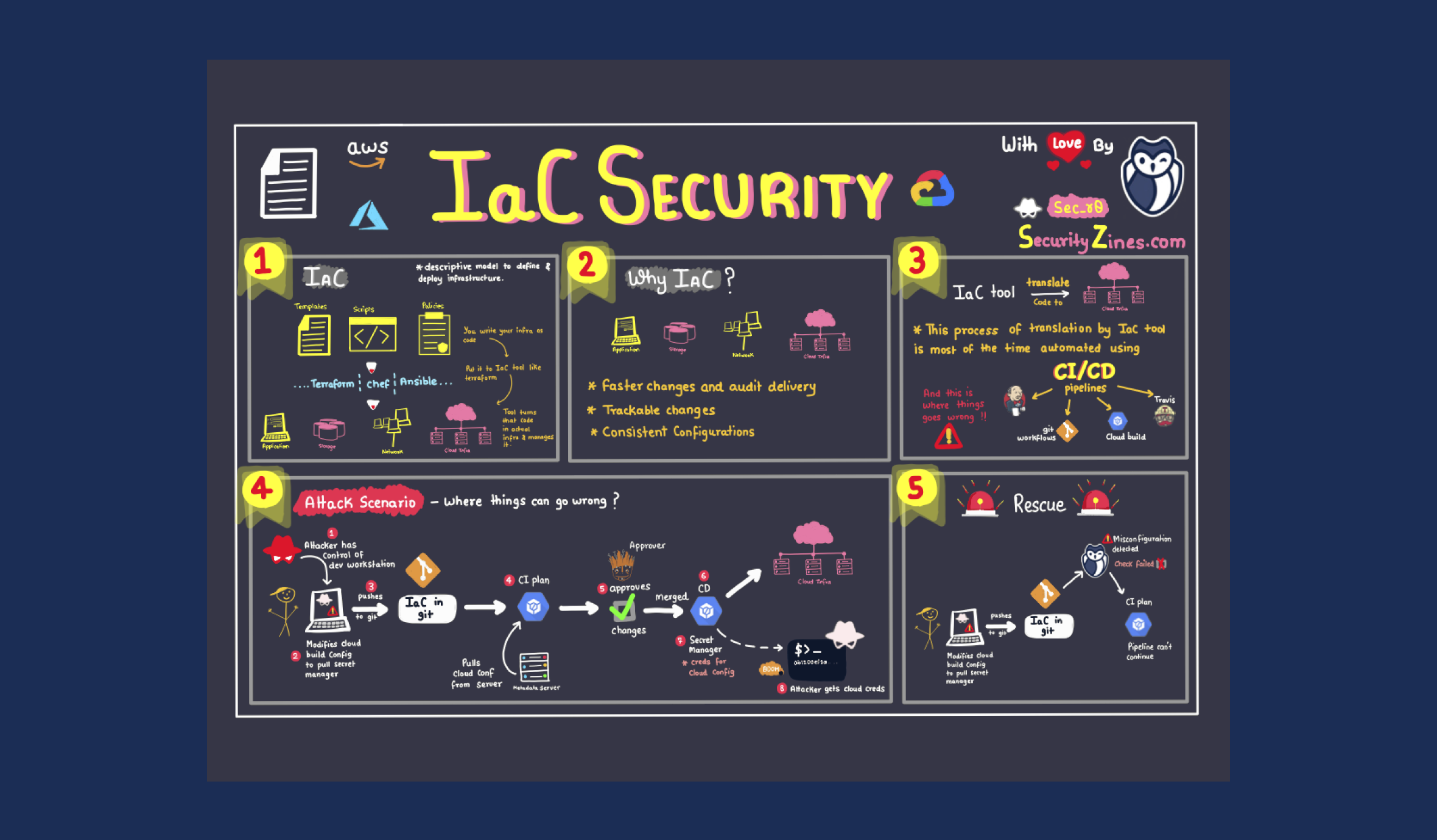
Best Practices for Scanning and Securing Infrastructure as Code (IaC)[cheat sheet included]

Checkov: Security & Compliance for Infrastructure-as-Code
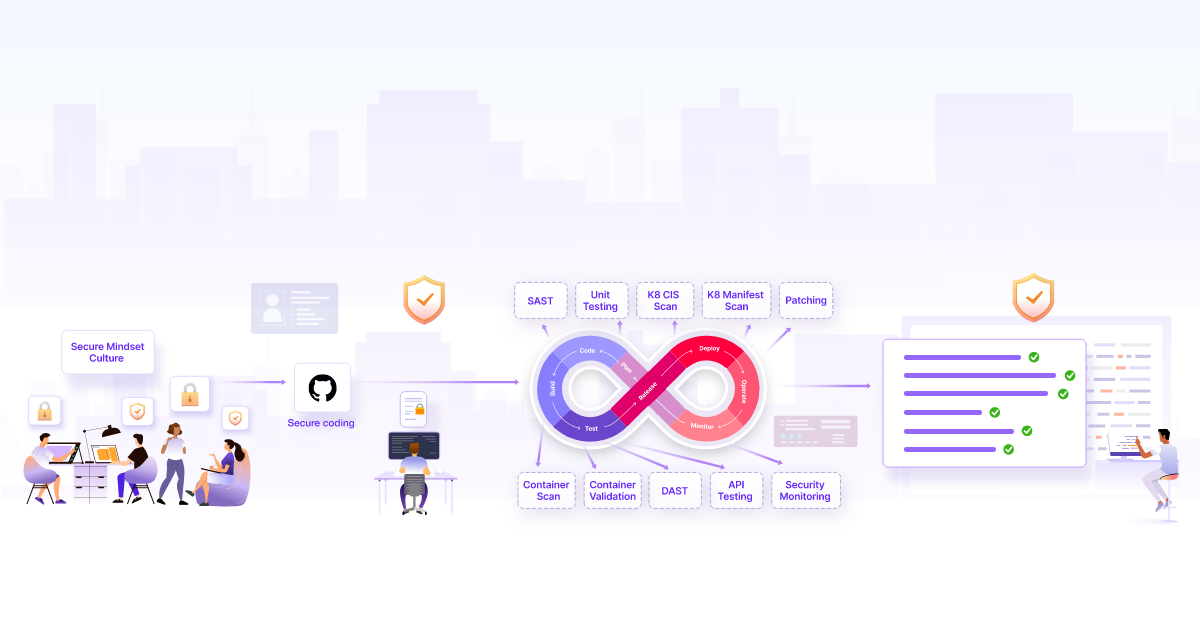
Implement DevSecOps to Secure your CI/CD pipeline

A Lap around Kubernetes Security & Vulnerability scanning Tools — checkov, kube-hunter, kube-bench & Starboard, by Cloud Journeys with Anindita

IaC security scanning tools, features and use cases
Common Security Risks in Infrastructure as Code - Coralogix

Cloud Code Security Cloud Code Security - Palo Alto Networks
de
por adulto (o preço varia de acordo com o tamanho do grupo)